PwnedList Shuts Down Because of Security Bug That Exposed Details for 866M Users
wnedList, a website that tells people when their website has been pwned and their sensitive credentials leaked online, has announced it will shut down on May 16, 2016.
The news comes after journalist Brian Krebs informed the company of a security issue that allowed a malicious attacker to monitor sensitive leaks for any domain, without going through the proper identity validation procedure.
PwnedList featured a flawed domain owner authentication procedure
By default, when a user creates an account on PwnedList and wants to follow when hackers leak access credentials online from his website (domain.com), he simply goes to his dashboard and adds domain.com as a site to monitor.
To validate his identity, PwnedList sends an email to the domain’s owner, which the user needs to validate by clicking a link that opens a confirmation page.
Security researcher Bob Hodges told Brian Krebs that the confirmation page is not tied in any way to the previous phase of the validation process, meaning that by altering a few parameters in the link’s URL, an attacker could validate himself as the owner of any domain.
Mr. Krebs performed a test to validate Mr. Hodges’ findings and soon he was receiving email alerts for any credentials exposed online for the Apple.com domain, which he obviously did not own.
Attackers could use PwnedList to track any website on the Internet
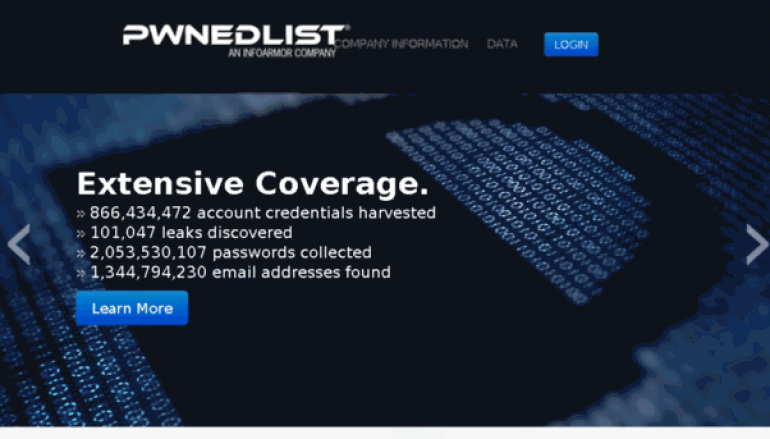
An attacker, using this vulnerability, could track leaked credentials for any website on the Internet, as well as receive reports for previously compromised domains. PwnedList claims to hold data on 866,434,472 compromised accounts from 101,047 leaks.
Mr. Krebs demonstrated the vulnerability to PwnedList founder Alen Puzic, now with InfoArmor, the company that bought the service. Following a successful demonstration, the service was temporarily brought down yesterday, and today features the following message, announcing the service’s shutdown.
Source | softpedia