Linux Cryptocurrency Miner Leverages Rootkit To Avoid Detection
Researchers from Trend Micro spotted a new cryptocurrency miner that leverages a rootkit component to hide its presence on the infected systems.
Cryptocurrency malware continues to be a privileged choice for crooks and the number of victims is rapidly growing.
Cryptocurrency miners are easy to detect due to the saturation of resources on the affected systems, but experts from Trend Micro spotted a new miner that leverages a rootkit component to hide its presence.
Even if the malware slows down infected systems abusing of their resources, the administrators will not be able to detect what process is causing it.
“We recently encountered a cryptocurrency-mining malware (detected by Trend Micro as Coinminer.Linux.KORKERDS.AB) affecting Linux systems,” reads the report published by TrendMicro.
“It is notable for being bundled with a rootkit component (Rootkit.Linux.KORKERDS.AA) that hides the malicious process’ presence from monitoring tools. This makes it difficult to detect, as infected systems will only indicate performance issues. The malware is also capable of updating and upgrading itself and its configuration file.”
The experts speculate that the infection vector could be an unofficial or compromised plugin such as a media-streaming software.
Once installed the initial executable (Trojan.Linux.DLOADER.THAOOAAK) will download a file from Pastebin that is a shell script. The file is saved as /bin/httpdns and a scheduled task is created to run /bin/httpdns every hour. The shell script is executed. /bin/httpdns contains a shell script that connects and downloads another base64-encoded text file.
The process will allow to download and execute a series of shell scripts that ultimately install the miner and then a rootkit to hide its presence.
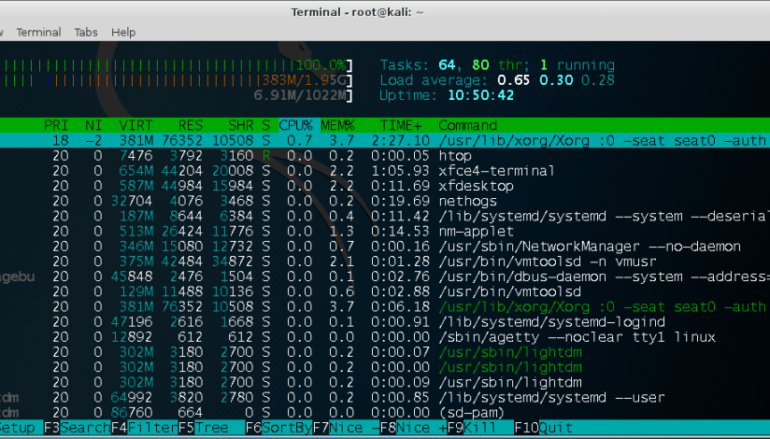
Experts pointed out that when the rootkit is not installed, administrators can easily detect the malicious process utilizing 100% of the CPU.
The following images show how the miner process is hidden by the rootkit.
Once the rootkit is installed, though, the process causing the high CPU is not visible even though the total system utilization is still shown as 100%.
This post Linux Cryptocurrency Miner Leverages Rootkit To Avoid Detection originally appeared on Security Affairs.








