Holy Water Targets Religious Figures and Charities in Asia
Holy Water – An APT group compromised a server hosting Web pages belonging mainly to religious figures and charities to carry out watering hole attacks.
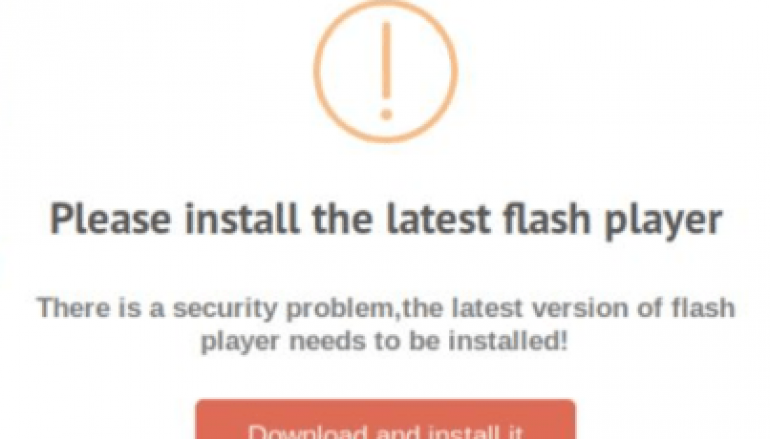
On December 4, 2019, Kaspersky experts discovered a watering hole attack, tracked Holy Water, aimed at an Asian religious and ethnic group. The campaign has been active since at least May 2019 and hit delivered fake Adobe Flash update warnings to the victims.
The experts believe that threat actors have been evolving, they were observed employing Sojson obfuscation, NSIS installer, Python, open-source code, GitHub distribution, Go language, as well as Google Drive-based C2 channels in their campaigns.
At the time it is still unclear the real target of the attacks.
“The watering holes have been set-up on websites that belong to personalities, public bodies, charities and organizations of the targeted group. At the time of writing, some of these websites (all hosted on the same server) are still compromised, and continue to direct selected visitors to malicious payloads.” reads the analysis published by Kaspersky Lab.
When a user visits one of the watering hole websites, a compromised embedded resource will load a malicious JavaScript hosted by one of the water-holed websites that gathers info on the visitor and determine whether it is a target.
If the visitor is a potential target, the attack chain starts, the JavaScript will load a second script that triggers the drive-by download attack displaying the victims a fake update pop-up.

The visitor is then tricked into installing the fake update that hides a malicious installer package that will set up a backdoor.
The analysis of the JavaScript script involved in the attack suggests that attackers might also target MacOS users.
Attackers used GitHub as the repository for the malicious executables employed in the attacks, GitHub disabled the repository on February 14 after Kaspersky reported it to them.
The repository has been online for more than nine months, GitHub provided the commit history, allowing the experts to gain a unique insight into the attacker’s activity and tools.
Experts found four executable hosted in the repository, an installer package, embedding a decoy legitimate Flash update and a stager, the Godlike12 Go backdoor that implements a Google Drive based C2 channel, and two versions of the open-source Stitch Python backdoor that were customized by the attackers.
“Digging into the repository for older commits, we also discovered a previous fake update toolset: a C installer bundling the legitimate Flash installer and a vanilla Stitch backdoor, as well as a C++ infostealer that collects information about host computers (OS version, IP address, hostname) and sends them over HTTP/S.” continues Kaspersky.
Experts noticed that attackers used a low-budget toolset but they spend a significant effort to evolve it.
“With almost 10 compromised websites and dozens of implanted hosts (that we know of), the attackers have set up a sizable yet very targeted water-holing attack. The toolset that’s being used seems low-budget and not fully developed, but has been modified several times in a few months to leverage interesting features like Google Drive C2, and would be characteristic of a small, agile team.” concludes Kaspersky.
“We were unable to observe any live operations, but some tracks indicate that the Godlike12 backdoor is not widespread, and is probably used to conduct reconnaissance and data-exfiltration operations. We were unable to correlate these attacks to any known APT groups.”
This post Holy Water Targets Religious Figures and Charities in Asia originally appeared on Security Affairs.





