Hackers Using COVID-19 Training Lure to Attack Office 365 Users
Coronavirus poses a huge impact globally, most of the countries in lockdown and some countries returning to some sort of normality.
Organizations also under risk of being impacted by a malicious coronavirus-related website depends on whether the country it is located in has gone back to business or is still under lockdown.
COVID-19 continues to pose a serious threat for organizations, so organizations implemented testing programs to prevent employees from infection.
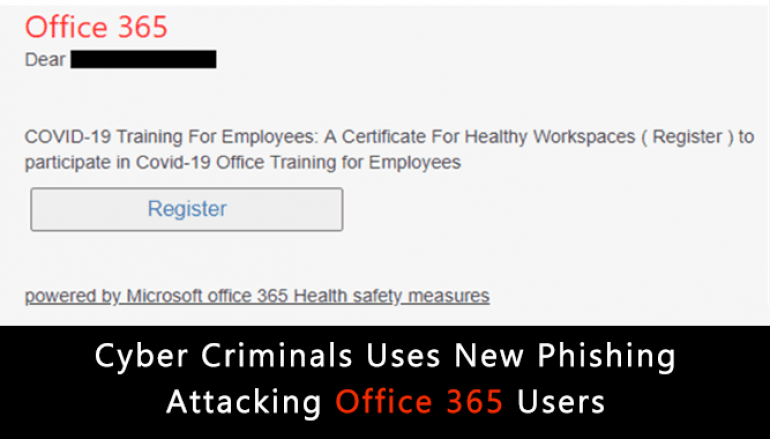
Checkpoint researchers observed the Cybercriminals distributing phishing emails and malicious files disguised as Covid-19 training materials.

The email is trying to lure the victim in signing up for a fake employee training web page, once the victim enters the login credentials it will be sent to the attacker’s server.
When the user opens the email and clicks on the attachment it displays the following image. But in the background, it downloads two malicious files.
Cyberattacks found to be increased by 16% in May when compared to March and April. Starting from June 2,451 new domains registered, out of 91 found malicious and 66 are suspicious.

Attackers taking advantage of the Coronavirus fear to continuously exploit online users by infecting their mobile with various tactics and techniques.
Cybercriminals continue to create phishing emails with this Coronavirus as the email subject or put in the email body to lure victims to click on links or download unwanted files.
This post Hackers Using COVID-19 Training Lure to Attack Office 365 Users originally appeared on GB Hackers.






