Hackers can use Web-Connected Car Washes to Physically Attack People
Researchers claim they can hack into internet-connected car wash machines from the other side of the world and potentially turn them into death traps.
In a presentation at the Black Hat conference in Las Vegas on Wednesday, Billy Rios, founder of security shop Whitescope, and Jonathan Butts, committee chair for the IFIP Working Group on Critical Infrastructure Protection, showed how easy it was to compromise a widely used car wash system: the Laserwash series manufactured by PDQ, based in Wisconsin, USA.
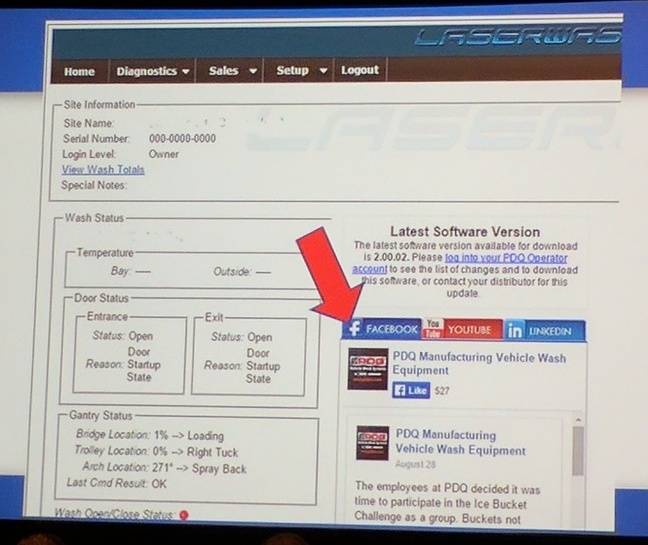
The pair found that Laserwash installations can be remotely monitored and controlled by their owners via a web-based user interface: the hefty gear has a builtin web server, and can be hooked up to the public internet allowing folks to keep an eye on their equipment from afar.
The hardware’s control system is an embedded WindowsCE computer powered by an ARM-compatible processor. However, Microsoft no longer supports the version of WinCE used in the kit, Rios said, meaning it may be possible to commandeer the machinery by exploiting security vulnerabilities lingering in the operating system.
However, there was no need to find and exploit old WinCE holes to remotely break into one of these bad boys. Once the infosec duo had found a suitable car wash connected to the web, the researchers found that the default password – 12345 – just worked. Once logged in from their browser, they were given full control of the system.
From there, they could prod the web app into doing things it really shouldn’t.
In their talk the pair showed how they managed to bypass the safety sensors on the car wash doors to close them on a car entering the washer.
“Car washes are really just industrial control systems. The attitudes of ICS are still in there. We’ve written an exploit to cause a car wash system to physically attack; it will strike anyone in the car wash. We think this is the first exploit that causes a connected device to attack someone. We controlled all the machinery inside the car wash and could shut down the safety systems,” he said. “You could set the roller arms to come down much lower and crush the top of the car, provided there was not mechanical barriers in place.”
The duo said they shared their findings with PDQ in February 2015, and kept trying to warn the biz for two years. It was only when their talk was accepted for Black Hat this year that the manufacturer replied to their emails, and then it turned out that it wasn’t possible to patch against the aforementioned exploits, we’re told.
PDQ spokesman Todd Klitzke said the car wash maker alerted its customers yesterday, coinciding with the conference presentation, and urged people to change their passwords from the default, or firewall off their equipment.
Source | The Register