DarkHotel APT Uses VPN Zero-Day in Attacks on Chinese Government Agencies
DarkHotel nation-state actor is exploiting a VPN zero-day to breach Chinese government agencies in Beijing and Shanghai
Chinese security-firm Qihoo 360 has uncovered a hacking campaign conducted by a DarkHotel APT group (APT-C-06) aimed at Chinese government agencies in Beijing and Shanghai. State-sponsored hackers used a zero-day vulnerability in Sangfor SSL VPN servers to gain access to victims’ networks.
The first Darkhotel espionage campaign was spotted by experts at Kaspersky Lab in late 2014, according to the researchers the APT group has been around for nearly a decade while targeting selected corporate executives traveling abroad.
Threat actors behind the Darkhotel campaign aimed to steal sensitive data from executives while they are staying in luxury hotels, they appeared high skilled professionals that exfiltrated data of interest with surgical precision and deleting any trace of their activity.
Since March, more than 200 VPN servers have been compromised by hackers, including 174 systems belonging to Chinese institutions abroad.
Experts observed Coronavirus-themed attacks launched by the group since March.
The coronavirus outbreak forced many individuals worldwide to work from home, including employees at state enterprises and institutions.
In this scenario, VPN are widely adopted, and it is not surprising that threat actors attempted to exploit vulnerabilities in VPN servers.
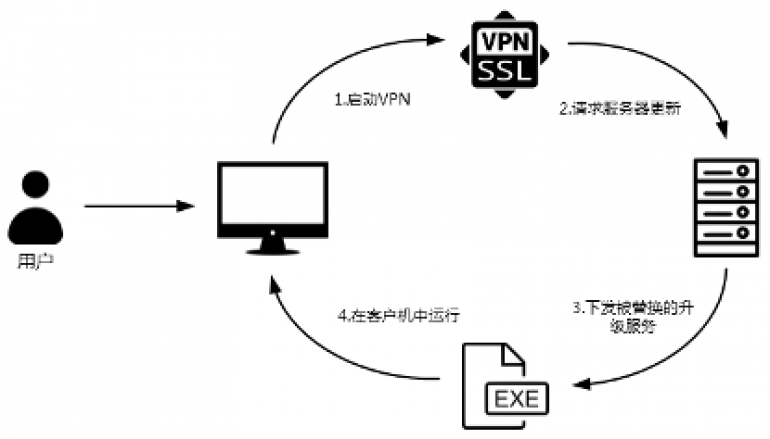
“Recently, Qihoo 360 captured malicious samples issued through hijacked security services of a domestic VPN vendor SangFor. The targeted attack was initiated by Darkhotel (APT-C-06), a Peninsula APT Group, targeting Chinese institutions abroad and relevant government units. Up to now, a large number of VPN users have been attacked.” reads the analysis published by Qihoo 360. “When users of the victim agency used VPN clients, the update process triggered by default was hijacked by the hackers. The update program was replaced and embedded with a backdoor.”

Once the attackers have breached the target Sangfor VPN server exploiting a zero-day vulnerability, they replaced the SangforUD.exe program with a backdoored version that is hard to distinguish.
The SangforUD.exe executable is an update for the Sangfor VPN desktop app.
“The vulnerability exists in an update that is triggered automatically when the VPN client starts to connect to the server. The client will obtain update from the configuration file at a fixed location on the connected VPN server, and download a program called SangforUD.exe. Due to the lack of security awareness of the developers, there are security risks in the entire update process. The client compares the version of the update program without doing any other security checks. This leaves a security flaw that the hackers can tamper the update configuration file and replace the update program after hacking the VPN server.” continues the researchers.
According to Qihoo360 the attacks are very sophisticated and concealed.
The security firm reported the zero-day vulnerability to Sangfor on April 3, the vendor confirmed that Sangfor VPN servers running firmware versions M6.3R1 and M6.1 are vulnerable.
Sangfor plans to release a security patched within tomorrow.
DarkHotel appears to very active in this period, experts reported that the group used other zero-day exploits in recently disclosed attacks.
The group exploited two vulnerabilities patched earlier this year in Firefox and Internet Explorer in attacks aimed at China and Japan.
Japan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) published a report containing technical details on attacks exploiting both flaws and aimed at Japanese entities
Two weeks ago, Reuters reported an attack against the World Health Organization and attributed it to the DarkHotel APT group.
This post DarkHotel APT Uses VPN Zero-Day in Attacks on Chinese Government Agencies originally appeared on Security Affairs.