Critical Vulnerability in SAP POS
A $25 Raspberry Pi or similar tiny PCs could be used to hack SAP POS systems due to a critical vulnerability. SAP POS is client-server technology that belongs to the SAP for Retail line-up, it is widely adopted, it has been estimated that it is used by 80 per cent of the retailers in the Forbes Global 2000.
The discovery was made by researchers at firm ERPScan that presented the hack at the Hack in the Box hacking conference held in Singapore last week. The attackers can exploit the vulnerability to steal customer’s card data and gain full control over the server.
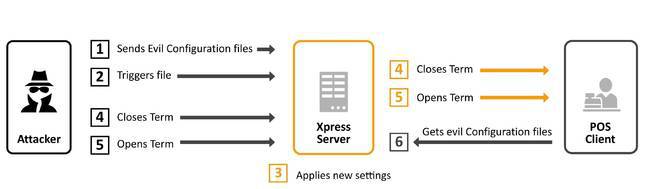
“Once you are in, you have unlimited control over the backend and front-end of the POS system, as the tool can upload a malicious configuration file on the SAP POS Xpress Server without any authentication procedure.” reads a security advisory published by ERPScan.
Attackers can provide Xpress Server new settings and apply them by sending certain commands to the Xpress server so that it restarts a POS terminal. Then the PoS terminal downloads the attacker’s configurations and applies them.
The company reported the issue to SAP in April, according to the experts the SAP POS Xpress Server fails the authentication checks for critical functionality.
This means that privileged functions could be accessed without any authentication.
“The vulnerabilities enable remote starting and stopping POS terminals,” states the analysis from ERPScan. “An attacker can remotely turn off all POS terminals within a merchant. Such DoS attack can be very costly for big retailers.”
The vulnerability could be exploited to record credit card number data and send them directly to a hacker’s server.
Unfortunately, similar problems affect many POS systems with equivalent architectures.
All vulnerabilities in SAP POS Retail Xpress Server have been addressed by SAP, organizations need to install the appropriate patches (SAP Security Note 2476601 and SAP Security Note 2520064) as soon as possible to protect their systems.