Technologies
In the IoT Ecosystem, Not too long ago in history, the idea that people and objects could be inter-connected would be considered absurd. Since the invention of the internet, that absurdity has since morphed into possibilities. Today, not only are
The Industrial Internet of Things (IIoT) is made up of interconnected sensors, instruments and other devices networked together with ICS/SCADA systems controlling water utilities, transportation systems, electric grids (the power grid) and other critical infrastructure systems. The Industrial Internet of
SCADA/ICS Dangers & Cybersecurity Strategies
Nearly 60% of surveyed organizations using SCADA or ICS reported they experienced a breach in those systems in the last year. Here are four tips for making these systems safer. A large number of government agencies and private organizations have
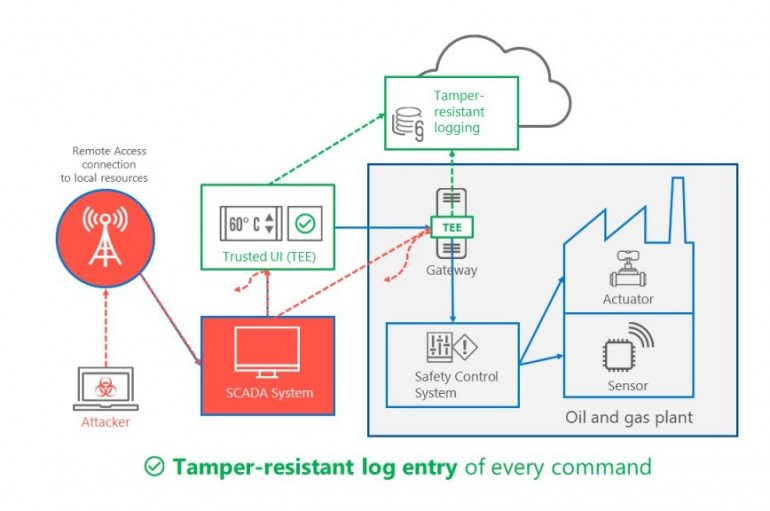
Microsoft last week unveiled Trusted Cyber Physical Systems (TCPS), a new solution designed to help protect critical infrastructure against modern cyber threats. Microsoft provided the recent Triton and NotPetya attacks as examples of significant threats hitting critical infrastructure. Triton was
Kaspersky-OS
On a day by day basis do IOT (Internet of Things) and SCADA become more integrated in our lives. However, with the introductions of these new technologies, security issues have been evolving at an unprecedented rate. Little did manufactures of
Data Diodes: Super Security or Super Pain?
Data diodes can create architectural complexity despite design simplicity of the data diodes themselves, but do they increase security? The concept of a data diode – a hardware device that only lets data out of the perimeter and prevents any
ICS Security: Essential Firewall Concepts
While there are many benefits that have come to ICS and SCADA networks through the increased use of standard networking and Internet technologies, it has made the need to secure them ever more critical. Firewalls play an important role in
Energy and electric utility organizations are facing a range of challenges requiring a reevaluation of the cyber security within their industrial control networks, endpoints and controllers. On the one hand, operators have to face losing access to phone lines, securing