Brazil Expert Discovers Oracle Flaw That Allows Massive DDoS Attacks
Oracle has just released a security update to prevent 2.3 million servers running the RPCBIND service from being used in amplified DDoS attacks.
The flaw was discovered by the Brazilian researcher Mauricio Correa, founder of Brazilian security company XLabs. The exploitation of this vulnerability could cause major problems on the Internet.
“A proof of concept (POC) made in only one XLabs server generated a traffic of 69 gigabits per second,” Mauricio told Cibersecurity.net.br.
At the time of the discovery, the expert queried Shodan and found that there were nearly 2.6 million servers running RPCBIND on the Internet. The multiplication of this exploit in a 2.6 million server farm leads to a frightening conclusion.
RPCBIND is software that provides client programs with the information they need about server programs available on a network. It runs on port 111 and responds with universal addresses of the server programs so that client programs can request data through RPCs (remote procedure calls).
These addresses are formed by the server IP pool plus port. Since its launch, RPCBIND has been receiving updates that cover several failures, including security. This, however, is the most serious finding so far.
The discovery of the crash began on June 11 this year. On that day, one of the web application firewalls (WAFs) installed in the XLabs SOC (security operations center) detected an abnormal pattern of network traffic that caught the eye of Mauricio.
The data showed that a DDoS attack was in progress, coming from port 111 of several servers, all from other countries.
“We then decided to open a server with port 111 exposed on the Internet, with the same characteristics as those who were attacking us and we were monitoring that server for weeks. We found that he was receiving requests to generate attacks, ” he explained.
After further analysis of the subject, it was possible to reproduce the attack in the laboratory.
“By analyzing the servers exposed at Shodan, the extent of the problem was confirmed,” continues Mauricio.
The problem discovered by Mauricio is worse than Memcrashed, detected in February of this year. In this type of distributed denial of service (DDoS) attack, the malicious traffic generated with the technique is greater than the once associated with the use of memcached, a service that does not require authentication but has been exposed on the internet by inexperienced system administrators. The service runs on UDP port 11211 and its exploitation by cybercriminals has already generated 260GB traffic according to Cloudflare company measurements.
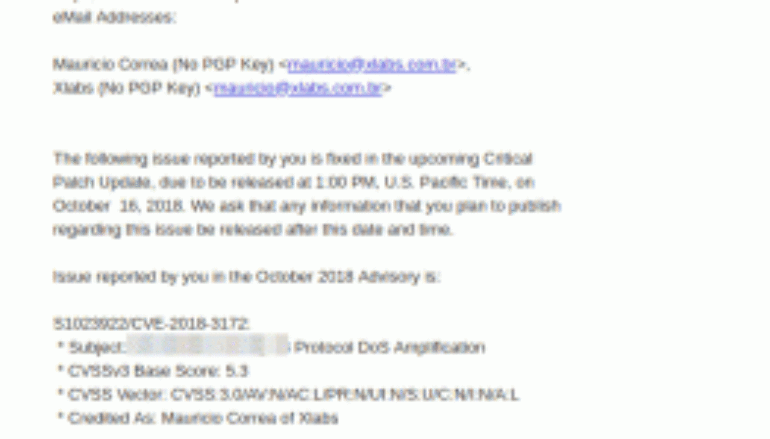
After developing the POC, Mauricio reported the problem to Oracle’s security team, since RPCBIND is a solution originating from Sun, which was acquired by the company in 2010.
He sent the information to Oracle so that the experts of the company could confirm and evaluate the problem. The confirmation arrived by email (see image), with the announcement of the publication date of the patch. It was on Tuesday, October 16, 2019 at 5:00 p.m., Brasilia time, 1:00 p.m. in San Francisco, California.
The Brazilian version of the post is available on the author’s blog.
This post Brazil Expert Discovers Oracle Flaw That Allows Massive DDoS Attacks originally appeared on Security Affairs.