Best Ways to Detect and Handle Suspicious Email Attachments
I’m going to share some tips on how to spot suspicious email attachments quickly and easily. We get so many emails daily that it can be easy for some to slip through the net. You need to be constantly on your guard especially when it comes to opening attachments.
Hackers use email attachments extensively to target the unsuspecting user. The attachments can contain Trojans and viruses but can also be used to hack your cell phone. They continually find clever ways to trick our automatic email security and filters to get into our inboxes in the first place. If they make it to your inbox simply opening an attachment can cause enormous problems.
If you get an email from an unknown source never open its attachment. While you can read the email without worry, providing that your computer is updated, you may want to avoid attachments. While email service providers typically scan and remove dangerous attachments, along with your own antivirus, some manage to slip through.
Even emails from supposed trusted sources could be phishing emails in disguise aiming to compromise your cell phone or computer using attachments.
Spotting a Suspicious Attachment by its Extension
When looking at an email attachment you should first consider its extension. The extension can help tell you the file type of the attachment. For instance, if your file ends with .jpg it’s an image. If it’s .avi it’s a video.
One extension you should usually avoid is .exe, which will execute an installation and that program may be malicious. While most email service providers block these files, they can sometimes slip through. A few other extensions to avoid include .jar, .cpl, .com, .bat, .msi, .js, .wsf, and so many more. If the extension looks odd, you should be suspicious.

What if it’s just an Office file? It should be fine, but you need to take some precautions. It may contain macros, which is a series of instructions that will execute a task. If your Office file ends with an m, it has macros. These include .docm. pptm, and .xlsm. While some safe files use macros, you should avoid unless you can verify it’s from a trusted source.
The rule of thumb is to only open extensions you can trust. Images files, macro-less Office files, and PDFs are usually fine, provided you have all the security updates in check.
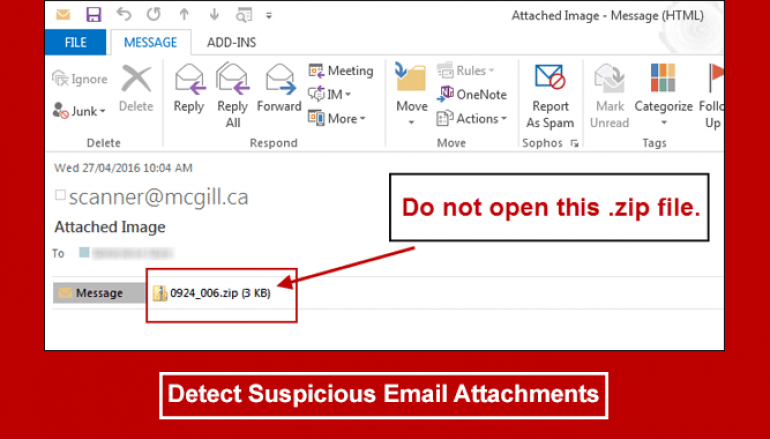
Is it an Encrypted Archive?
Archive files are useful for many reasons. They allow people to compress multiple files into one package, making it easier to send. However, they can be used by hackers as well. If you get an email and it has an archive extension, such as .7z, .rar, or .zip, and requires you to enter a password, it may be suspicious.
Why do they password protect? It encrypts the archive so that any virus scanner cannot see it. They may do this to hide malware. Of course, it may be because it contains sensitive information, so you never know. Once again, make sure it comes from a trusted source before you open.
Who is the Sender?
As we should know, you can usually trust someone who sends you an attachment if you know them. If you don’t know the person, it may be malware. However, someone you know could be infected themselves, and the malware will send you a file under the person’s name to build trust, so beware. If someone you know sends you a macro Office file without telling you, exercise caution.
You should contact the person to see if they sent the suspicious attachment. If they did, you can open it, but if they didn’t, discard their email and tell them that they’ve been hacked.
What does the Email Say?
Before you open an attachment, read the email. If it appears to be a trusted source, but the contents don’t seem like something they would send, it could be a sign that it’s malware. These are typically done by phishing scams, who will disguise themselves as a bank or a site that has your payment info, telling you to enter your information due to your account potentially being compromised.
These emails may be poorly written with typos everywhere and awkward sentences. If you get an email from Amazon, and tells you to download something and then run it, it may be a sign of a scam. Most businesses would not make you do this.
Virus Alerts
If your email is from a major service provider, like Yahoo!, Gmail, or Hotmail, they will scan for attachments and warn you if they’re potentially dangerous, making you not want to open it. Of course, the email may claim that the antivirus alert is due to a bug or something, but that’s obviously a lie.
If you download the attachment anyway, and your own antivirus program is telling you not to do it, listen. They’re obviously detecting something bad. However, sometimes your antivirus may say nothing. This doesn’t mean it’s safe, as antivirus programs do mess up. Use your best judgment when opening files.
Be Cautious and Stay Safe!
When looking at an attachment, you should be skeptical about its contents and assume that it may be dangerous. Never open an attachment unless you know for sure that it’s from a trusted source, and you’ve been expecting it. Also, look at the extension. PDFs, images, and videos should be fine, provided you’re updated. But even then, tread lightly.
Usually, your email service allows you to preview attachments without downloading, so use that to your advantage. Look at its contents, and if everything seems fine, download away. While you shouldn’t be scared of everything you receive, you should be alert.
This post Best Ways to Detect and Handle Suspicious Email Attachments originally appeared on GB Hackers.






