Posts From CCME
Critical Zoom Vulnerability Allows Hackers to Steal your Windows Password & Escalate Privileges with macOS
A critical vulnerability with the Zoom client for windows allows attackers to steal Windows login credentials. Zoom is an online video communication platform that has features such as video conferencing, online meetings, chat, and mobile collaboration. Zoom usability is high
An American healthcare provider whose patients’ records were allegedly published online in a ransomware attack has told patients their data is secure. Affordacare runs an urgent care walk-in clinic network out of five locations in Texas. The organization was hit
Ransomware Payments on the Rise
More ransomware victims than ever before are complying with the demands of their cyber-attackers by handing over cash to retrieve encrypted files. New research published March 31 by CyberEdge shows that both the number of ransomware attacks and the percentage
A cybersecurity company has launched a lockdown-friendly hacking competition that doesn’t require any travel or socializing. Participants of Cyber 2.0’s new Home Hackers Challenge can compete for a cash prize without having to leave their houses. The competition is open
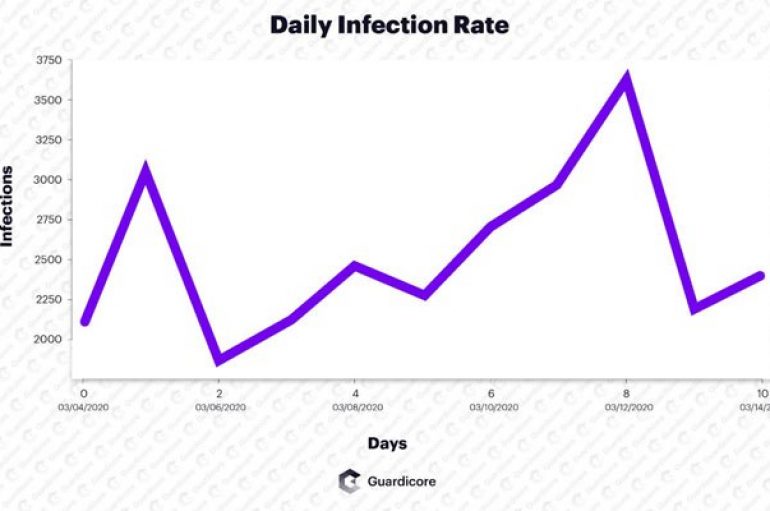
Cybersecurity researchers spotted a crypto-mining botnet, tracked as Vollgar, that has been hijacking MSSQL servers since at least 2018. Researchers at Guardicore Labs discovered a crypto-mining botnet, tracked as Vollgarbotnet, that is targeting MSSQL databases since 2018. The botnet is used
UK businesses could be putting customer data at risk by having a low understanding of important data protection legislation. Research from IONOS has shown that 44% of IT decision makers in the UK do not have a comprehensive understanding of
Researchers published proof-of-concept (PoC) exploits for the CVE-2020-0796 Windows flaw, tracked as SMBGhost, that can be exploited for local privilege escalation. Researchers Daniel García Gutiérrez (@danigargu) and Manuel Blanco Parajón (@dialluvioso_) have published proof-of-concept (PoC) exploits for the CVE-2020-0796 Windows vulnerability,
Chinese conspiracy theories that COVID-19 was some kind of US military bioweapon date back to January, months before a foreign ministry official in Beijing began to spread the same fake news, according to a new study. An analysis from the
Researchers found a piece of Raccoon Stealer that abuse of Google Cloud Services and leverages multiple delivery techniques. Racoon malware (aka Legion, Mohazo, and Racealer) is an info-stealer that recently appeared in the threat landscape that is advertised in hacking forums. The malware
Online threats have risen by as much as six-times their usual levels over the past four weeks as the COVID-19 pandemic provides new ballast for cyber-attacks, according to Cloudflare. The web security and content delivery vendor analyzed UK traffic figures
A new partnership has been announced between the National Cyber Security Centre (NCSC) and the IASME Consortium to relaunch the Cyber Essentials Scheme, with IASME as the sole certification body. The NCSC has carried out research, determining the path to
A company claiming to provide “the world’s most secure online backup” leaked metadata and customer information in over 135 million records after misconfiguring an online database, Infosecurity has learned. The team at vpnMentor discovered the privacy snafu as part of
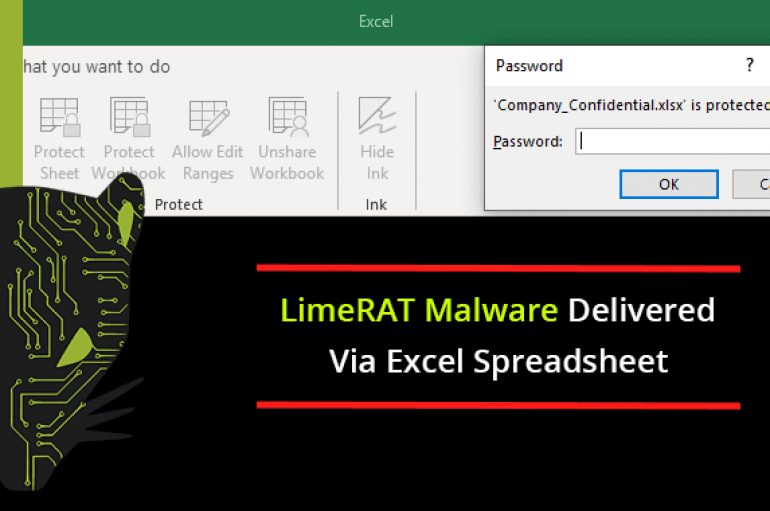
A new malware Campaign discovered using password-protected Microsoft Excel spreadsheets to deliver LimeRAT malware. Security researchers from Mimecast discovered the attack campaign, uses an email method to deliver the read-only weaponized Microsoft Excel spreadsheets. The Microsoft Office is one of
Researchers from Wordfence uncovered two RCE vulnerabilities in WordPress SEO plugin called Rank Math let hackers hijack nearly 200,000 vulnerable Websites and gain remote access. Rank Math is an SEO plugin for WordPress and it gives various SEO features such
Hotel chain Marriott International announced today that it has suffered a second data breach. According to an incident notification published on their website, the company spotted unusual activity occurring in an app that guests use to access services during their
Holy Water – An APT group compromised a server hosting Web pages belonging mainly to religious figures and charities to carry out watering hole attacks. On December 4, 2019, Kaspersky experts discovered a watering hole attack, tracked Holy Water, aimed