Posts From CCME
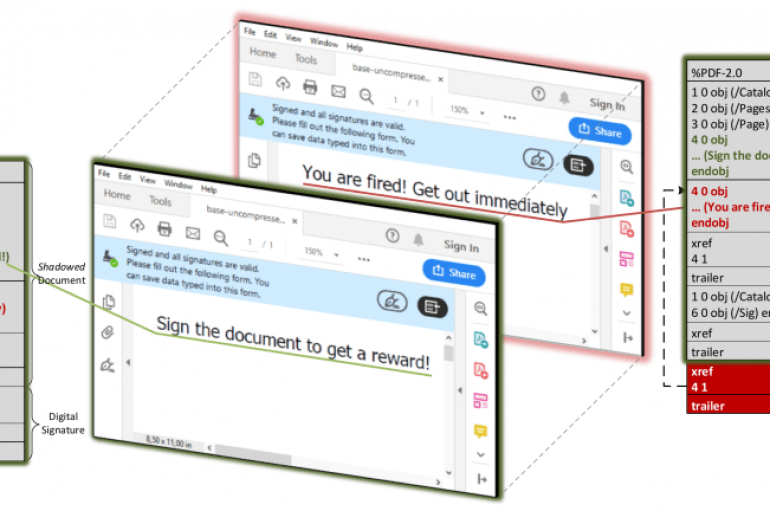
Boffins from the Ruhr University Bochum (Germany) have disclosed a series of new attack methods, dubbed Shadow attacks, against signed PDF files. Security researchers from the Ruhr University Bochum (Germany) have devised a series of new attack techniques, dubbed Shadow
Digital banking app Dave.com discloses a security breach after the known threat actor ShinyHunters leaked 7 million user records on a crime forum. The popular digital banking app Dave.com discloses a security breach after the known threat actor ShinyHunters leaked 7,516,625 user
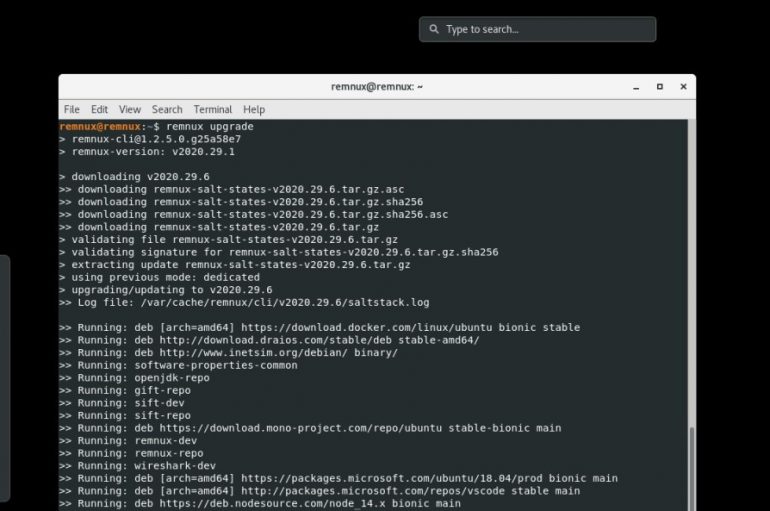
A new version of the REMnux Linux toolkit for malware analysts is available for download, it includes a huge set of tools for professionals. REMnux is a Linux toolkit for reverse-engineering and dissecting software, it includes a collection of free
REMnux is a Linux distro for malware researchers that has a curated collection of free tools used for examining executables, documents, scripts, and other forms of malicious code. The tools help researchers to find, install, and configure the tools. The
The National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) have recommended that all DoD, NSS, DIB and US critical infrastructure facilities take immediate actions to secure their operational technology (OT) assets. The advice comes in light
Cisco fixed CVE-2020-3452 high-severity path traversal flaw in its firewalls that can be exploited by remote attackers to obtain sensitive files from the targeted system. Cisco addressed a high-severity path traversal vulnerability in its firewalls, tracked as CVE-2020-3452, that can
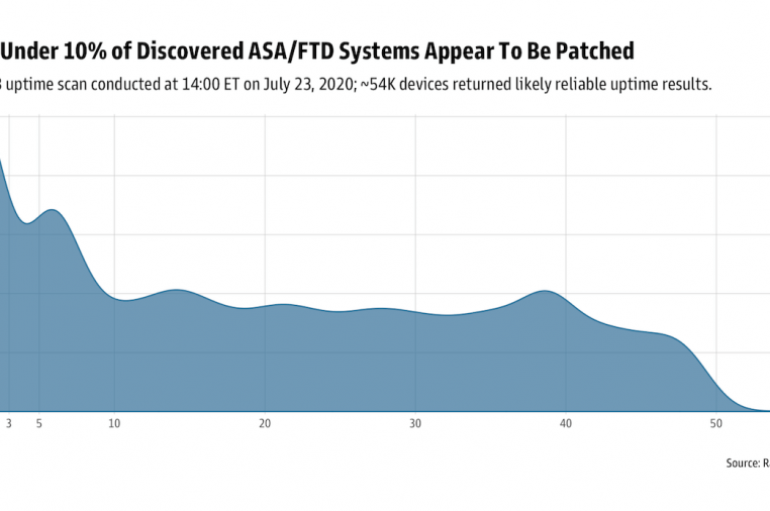
Hackers Exploited CVE-2020-3452 Flaw in Cisco ASA & FTD Within Hours After the Disclosure
Cisco fixed a high-severity path traversal vulnerability CVE-2020-3452 with Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software. The vulnerability allows a remote attacker to launch a directory traversal attack that allows attackers to read sensitive
The Internet Society, a global non-profit organization dedicated to ensuring the open development, evolution and use of the internet and AFRINIC, the Regional Internet Registry (RIR) for the African region, have today announced the launch of a new collaborative effort
New questions are being asked of Twitter’s cybersecurity posture after the social network revealed that hackers managed to access the DMs of 36 high-profile accounts in a recent breach, including one Dutch politician. The firm revealed the news in an
Garmin Outage Could Ground Aircraft
Pilots using the flyGarmin app may be forced to ground their aircraft after a suspected ransomware attack against the smart device maker appeared to take out key services. As of Thursday evening EDT, flight plan filing, account syncing and database
ADIF, a Spanish state-owned railway infrastructure manager under the responsibility of the Ministry of Development, was hit by REVil ransomware operators. Administrador de Infraestructuras Ferroviarias (ADIF), a Spanish state-owned railway infrastructure manager was hit by REVil ransomware operators. ADIF (Administrador de Infraestructuras Ferroviarias) is charged with the management of most
Blackbaud Breach Hits Nine More Universities
A combined ransomware and data breach attack on a US cloud computing provider in May has affected many more universities and non-profits than at first thought. Infosecurity reported on Wednesday how the University of York in northern England had notified
Facebook announced a new privacy feature that adds another layer of security to your private messages and stops people from accessing them. The new app lock feature helps prevent other people from accessing your chats. The app lock is now
Last week several high-profile Twitter accounts hacked including Biden, billionaires, and corporate accounts hacked in Bitcoin scam. The high-profile accounts were hijacked in a quick rapid session and message posted to trick the users sending payments to a BTC address
The COVID-19 pandemic has led to a major boost in cybersecurity job vacancies in the US, data from the Cybersecurity Jobs Report: Q2, has revealed. The study, produced by the International Consortium of Minority Cybersecurity Professionals (ICMCP) and CyberVista, indicates
Email account takeover (ATO) attacks often last for over a week and result from employees reusing passwords across multiple sites, according to new research from Barracuda Networks. The security vendor teamed up with researchers at UC Berkeley to study the