Posts From CCME
Sebastien Kaul, a security researcher based in Berlin, has discovered a poorly secured database owned by communication firm Vovox that contained left names, phone numbers, tens of millions of SMS messages, temporary passwords, two-factor codes, shipping alerts, and other information
Kaspersky revealed that the CVE-2018-8589 Windows 0-day fixed by Microsoft Nov. 2018 Patch Tuesday has been exploited by at least one APT group in attacks in the Middle East. Kaspersky Lab experts revealed that the CVE-2018-8589 Windows zero-day vulnerability addressed
At the second annual Infosecurity North America conference at the Jacob Javits Convention Center in New York, Tom Brennan, US chairman, CREST International, moderated a panel called Securing the Workforce: Building, Maintaining and Measuring an Effective Security Awareness Program to
#InfosecNA18: Finding and Keeping Security Teams
Finding and keeping talent in the cybersecurity industry is a challenge for organizations of all sizes around the globe. As a result, the talent market is highly competitive, which is why a panel of experts came together at this year’s
Most IT Pros Fear AI-Powered Attacks
Over 80% of security professionals are concerned about the prospect of attackers using artificial intelligence (AI) against their organization, according to new research from Neustar. The global information services provider polled 301 IT and security professionals across EMEA and the
Cyber-attacks are the number one business risk in the regions of Europe, North America and East Asia and the Pacific, according to a major new study from the World Economic Forum (WEF). Its Regional Risks for Doing Business report highlights
New research from SailPoint has revealed that poor staff cybersecurity behaviors within organizations are getting worse, despite a greater focus on security awareness in the workplace. The firm quizzed 1600 global employees, discovering that 75% of respondents reuse passwords across
A security researcher at Imperva recently identified a vulnerability within Facebook that could have allowed other websites to extract private information about users and their contacts. Discovered by Imperva security researcher Ron Masas, the vulnerability reportedly preyed on the unique
Nearly 4,000 Breaches Disclosed in 2018
While it is likely that the breach activity of 2018 won’t reach the level of 2017, a look back at the first nine months suggests that 2018 is on pace to be another significant year for breaches, according to Risk
WannaCry ransomware is still the most widespread cryptor family and has hit almost 75,000 users as of Q3 2018, according to new research from Kaspersky Lab. The firm discovered that since the WannaCry outbreak in May 2017 that cost the
A Canadian university shut down its entire network last week in response to a cryptomining attack, highlighting the potential disruption that can be caused by this relatively new strain of malware. St Francis Xavier, which claims to offer the country’s
Based on the results of a new survey, the vast majority of IT security pros fail to understand the actual risks of short-lived but dangerous phishing attacks on the web, said SlashNext. Conducted over a five day period, a query
Researchers from Trend Micro spotted a new cryptocurrency miner that leverages a rootkit component to hide its presence on the infected systems. Cryptocurrency malware continues to be a privileged choice for crooks and the number of victims is rapidly growing.
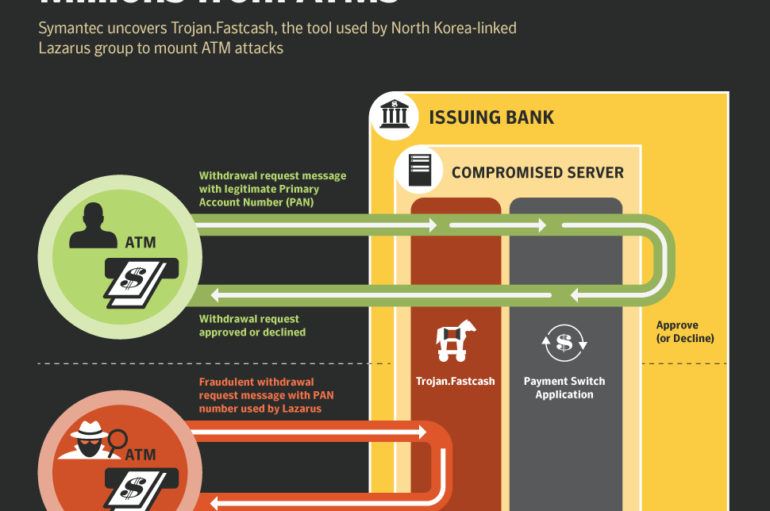
North Korea-linked Lazarus Group has been using FastCash Trojan to compromise AIX servers to empty tens of millions of dollars from ATMs. Security experts from Symantec have discovered a malware, tracked as FastCash Trojan, that was used by the Lazarus
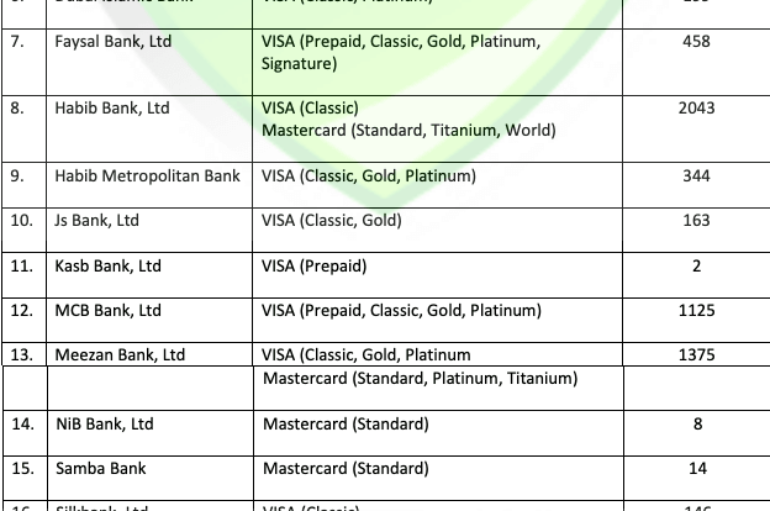
Data From ‘Almost All’ Pakistani Banks Stolen, Pakistani Debit Card Details Surface On The Dark Web
According to the head of the Federal Investigation Agency’s (FIA) cybercrime wing.almost all Pakistani banks were affected by a recent security breach. Almost all Pakistani banks were affected by a recent security breach, the shocking news was confirmed by the
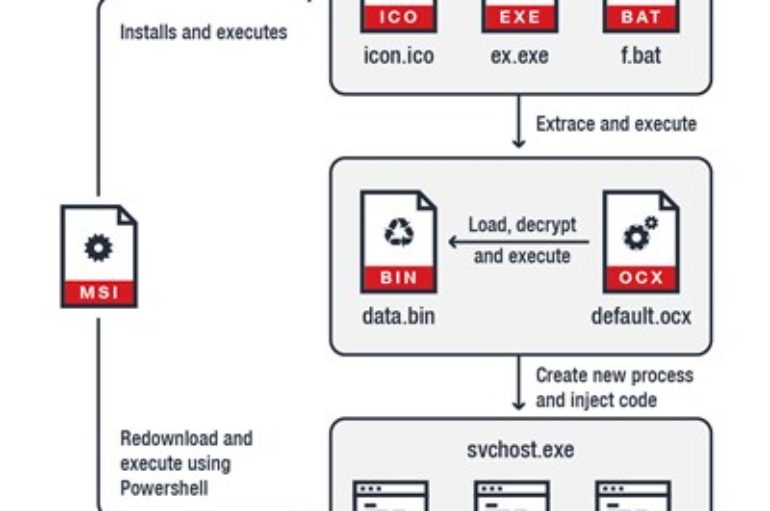
Stealthy Crypto-Mining Malware Evades Detection
Cryptocurrency mining has become a fairly easy way to manufacture currency, and according to Trend Micro, a new cryptocurrency-mining malware uses evasion techniques, including Windows Installer, as part of its routine. In the cryptocurrency miner identified as Coinminer.Win32.MALXMR.TIAOODAM, researchers noted