Posts From CCME
Google revealed a shocking statement that they stored enterprise G Suite customers login password in plain text over a decade. According to Google’s privacy and security policy, all the customers and users login credentials must be stored in an encrypted
How Selfie Authentication Process Improve the Security Along With Other Authentication Methods
Digital identity has two different domains – one is identity proofing and the other is authentication, where both have been unique to each other for many years. Businesses have now utilized several identity proofing methods to distinguish users’ identities by
Fraud Attacks from Mobile Spiked 300% in Q1
Fraud attacks from mobile apps spiked by 300% in the first quarter of 2019, according to new researcher from RSA. Published today, the Fraud Attack Trends: Q1 2019 report found that the total fraud attacks from rogue mobile applications on
Firmware Vulnerability in Mitsubishi Electric
A vulnerability in Mitsubishi Electric‘s MELSEC-Q Series Ethernet Module could allow a remote attacker to gain escalated privileges, according to an ICS-CERT advisory. Reported by Nozomi Networks, the vulnerability “could allow an attacker to render the PLCs statue in fault
FCA: GBP27m Lost to Crypto Scams Last Year
The UK’s financial regulator has warned that GBP27m was lost in the last financial year to scams promising big returns on cryptocurrency and foreign exchange (forex) investments. The Financial Conduct Authority (FCA) claimed that investors lost on average GBP14,600 to
A new massive database uncovered that contains nearly 49 million of Instagram Influencer’s, celebrities and brand account contact information leaked online. Security researcher Anurag Sen discovered this unprotected database and reported to Tech Crunch, in result, owners have been notified
The number of DDoS attacks increased by 84% in the first quarter of 2019 compared to Q4 2018, according to new research from Kaspersky Lab. The global cybersecurity company’s findings, detailed in its DDoS Attacks in Q1 2019 report, come
The operating system of your computer is the most important part of your network that needs an update from the time. This is essential to make sure that you can keep track of whatever updates is happening within the cyber
A fifth of the world’s most popular Docker containers contain a security issue which could make them vulnerable to attack in some circumstances, a researcher has discovered. Kenna Security principal security engineer, Jerry Gamblin, explained that after recent Cisco Talos
KnowBe4 Announces Acquisition of CLTRe
KnowBe4 has announced the acquisition of CLTRe, adding the capability to measure security culture into its portfolio. Led by Kai Roer, CLTRe is a Norwegian company focused on helping organizations assess, build, maintain and measure a strong security posture. It
A recent MuddyWater campaign tracked as BlackWater shows that the APT group added new anti-detection techniques to its arsenal. Security experts at Cisco Talos attributed the recently spotted campaign tracked as “BlackWater” to the MuddyWater APT group (aka SeedWorm and
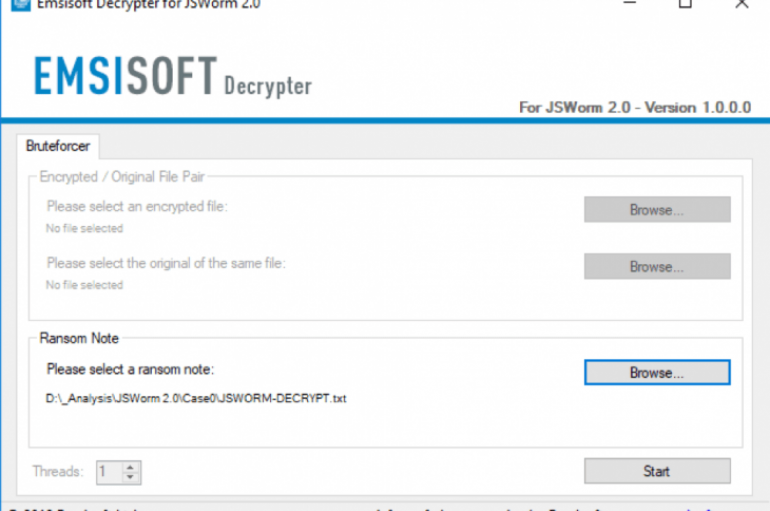
Good news for the victims of the JSWorm 2.0 ransomware, thanks to experts at Emsisoft they can decrypt their file for free. Experts at Emsisoft malware research team released a decrypter for a recently discovered ransomware tracked as JSWorm 2.0.
Encryption continues to be a challenge for companies, as only a quarter of organizations admit to using it for at-rest data, and for emails and data centers. According to research by Thales and IDC, encryption for email is only adopted
Cyber-criminals continue to grow more sophisticated, developing advanced attack methods, including tailored ransomware, according to the Q1 Global Threat Landscape Report, published today by Fortinet. In addition to targeted attacks, criminals are also using custom coding, living-off-the-land (LotL) and sharing
Managing the organization’s critical patches to keep computers up to date is very hard since there are hundreds of products and software deployed within the organization network. In this case, an enterprise with multiple servers and computers, ensuring that all
Online Account Hijacker Forum OGUsers Hacked
An online forum used by those involved in online account hijacking has been breached, according to KrebsonSecurity. An attack on OGUsers.com leaked the personal information of nearly 113,000 people. Krebs reportedly received a copy of the database, which included usernames,