Posts From CCME
Online education platform Thinkful has suffered a data breach which may have given hackers access to users’ accounts. The training site for developers notified all of its users by email that an unspecified number may have had their “company credentials”
In order to exploit the vulnerability attacker should have applicable tool or technique that connect to the system weakness. Following are the top sources to trace new vulnerabilities. National Vulnerability Database Common Vulnerabilities And Exposures VulnDB – Vulnerability Intelligence DISA
Big Data analytics is emerging from today’s technology as people are demanding better ways to protect their Big data. Keep reading to find out how Hadoop via cybersecurity methods in this post. What is Hadoop? Hadoop is a Java-based, open-source
12 Most Popular Deep Learning Libraries 2019
Deep learning libraries are essentially sets of functions and routines written in a given programming language. A large set of deep learning libraries can make it quite simpler for data engineers, data scientists and developers to perform tasks of any
What Is A Bug Bounty Program? A Bug bounty program is also known as vulnerability rewards program (VRP) is the one where security researchers can disclose vulnerabilities and can receive recognition and compensation for reporting bugs. The threat to business
Facebook Suspended More Than 10,000 Apps That Associated with 400 Developers for Abusing FB Privacy
Facebook announced that they suspended “tens of thousands” of apps associated with 400 developers due to the privacy concern, and pose a threat to the Facebook community. After the Cambridge Analytica scandal that affected 87 Million Facebook Users, Facebook continuously
Wireshark 3.0.5 has been released with the new Qt version and fix for other vulnerabilities. The Qt is the library used in Wireshark to build the UI. The Wireshark is the famous protocol analyzer tool used for protocol analysis, troubleshooting,
Senior Execs Shun Cyber Risk as Concerns Grow
Nearly 80% of global organizations now rank cyber-risk as a top-five business concern, but just 11% are highly confident they can assess, prevent and respond effectively to attacks, according to new research from Marsh and Microsoft. The insurer has teamed
US Air Force Bids $95m Cybersecurity Contract
The US Air Force is requesting quotes from vendors that can provide support for a cybersecurity project under a contract worth up to $95m. Vendors of any size are being sought to support an experimental cybersecurity platform development team that
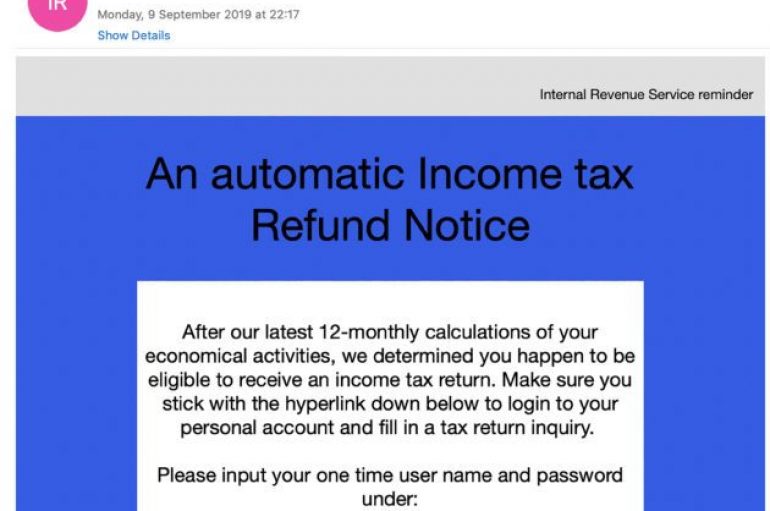
Cofense researchers spotted a phishing campaign that is targeting taxpayers in the United States to infect them with the Amadey malware. Security experts at Cofense uncovered a phishing campaign that is targeting taxpayers in the United States attempting to infect
Critical Vulnerability in D-link DNS-320 Devices let Hackers to Execute Remote Code and to Steal Data
D-link DNS-320 Devices have used as an ideal backup solution, it offers an effective way to share documents, music, videos, and photos with anyone that connected in your network. CyStack security researcher, Trung Nguyen, detected a remote code execution vulnerability
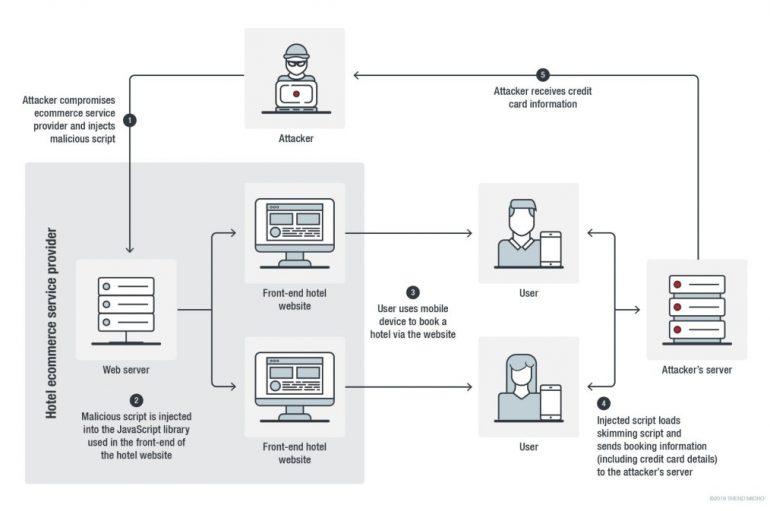
Trend Micro researchers reported that a Magecart group has hacked the websites of two hotel chains to inject scripts targeting Android and iOS users. Researchers discovered a series of incidents involving software credit card skimmer used by Magecart to hit
Critical Vulnerability in Harbor let Hackers to Escalate Privilege by Sending Malicious Request
Harbor is a cloud-native registry that offers rich functions in container management that stores signs and scan images for vulnerabilities. It can be integrated with Docker Hub, Docker Registry, Google Container Registry, and other registries. Security researchers from the cloud
Threats actors behind the Smominru botnet compromised nearly 90,000 windows computers in last month using EternalBlue exploit and performing brute force attacks on MS-SQL, RDP, Telnet services. Researcher uncovered that the botnet infected more than 4000 systems, network daily, and
WeWork’s WiFi Security Worryingly Weak
A lack of security on WeWork’s WiFi network has left sensitive user data exposed. In August, Fast Company revealed that WeWork had used the same WiFi password at many of its rentable shared co-working spaces for years, a password that
The City of Los Angeles and IBM are joining forces with the LA Cyber Lab to help local businesses combat cybercrime. In a new project announced by IBM Security on September 17, the American multi-national IT company will provide technologies