Posts From CCME
Fastly to Acquire Signal Sciences
California edge cloud computing company Fastly has entered into a definitive agreement to acquire American cybersecurity company Signal Sciences. Stock in Fastly rose by over 7% to $95.98 a share following the announcement of the impending $775m deal on Thursday
Android Users Bugged by Fake Popups
Google Android users were pestered last week by a series of fake notifications popping up on their devices. According to Paul Ducklin of Naked Security by Sophos’, the string of phony popups first became an annoyance for users of the
QBot Trojan operators are using new tactics in their campaign to hijack legitimate email conversations to steal sensitive data from the victims. Researchers from Check Point are warning of a new trend observed in QBot Trojan campaign targeting Microsoft Outlook
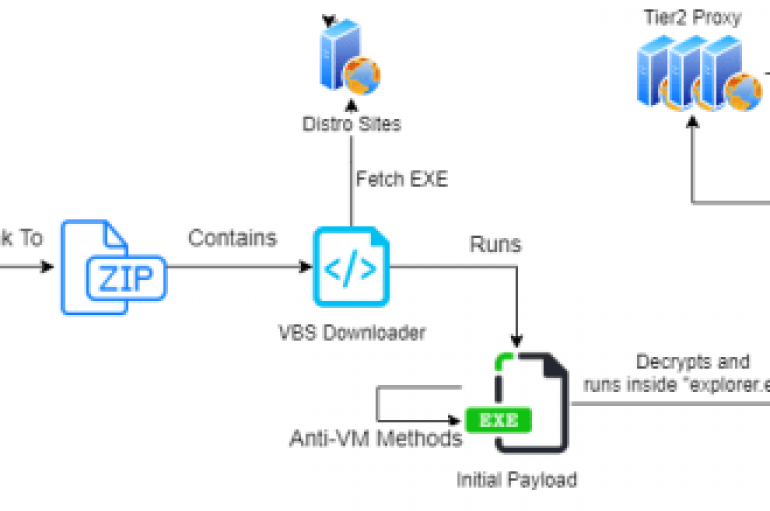
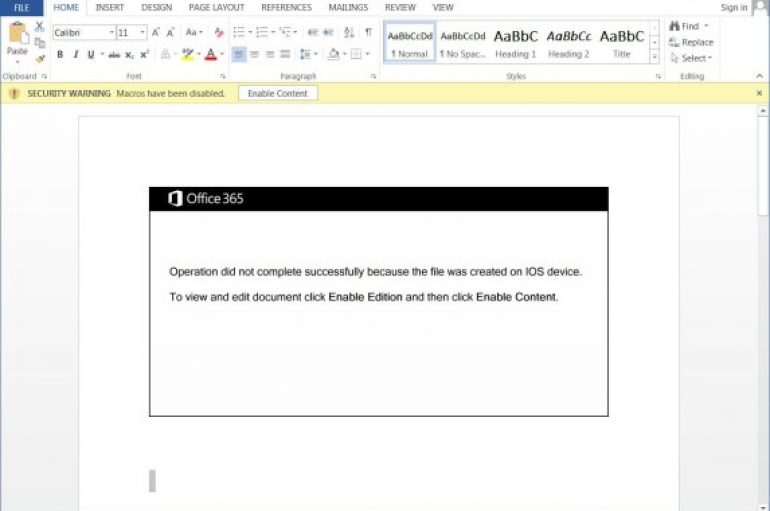
In August, the Emotet botnet operators switched to a new template, named ‘Red Dawn,’ for the malicious attachments employed in new campaigns. The notorious Emotet went into the dark since February 2020, but after months of inactivity, the infamous trojan has surged back
Researchers from White Ops discovers several Android apps in the official Play store which installed on users’ mobile devices the Terracotta ad fraud malware. Researchers from security firm White Ops discovered several Android apps in the official Play Store that
FBI Warns of an Increase in Online Romance Scams
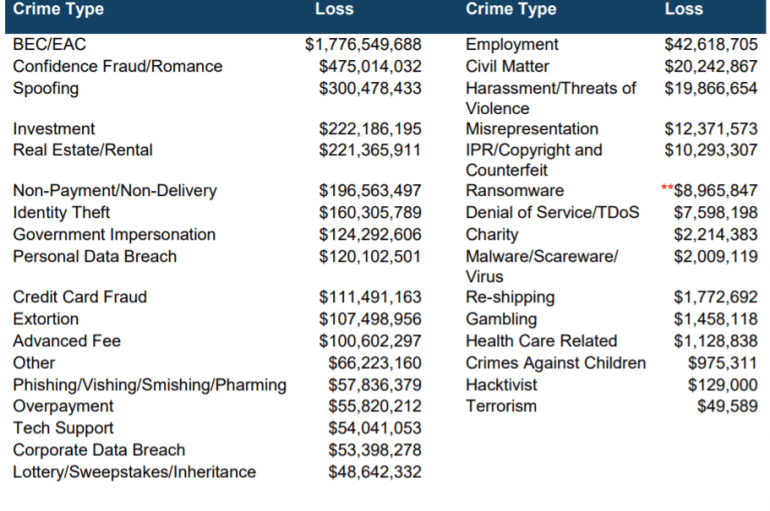
The FBI is warning of online romance scams and related financial losses, overall losses associated with those complaints exceeded $475 million. The Federal Bureau of Investigation warns of online romance scams (also known as confidence fraud), an ongoing criminal activity
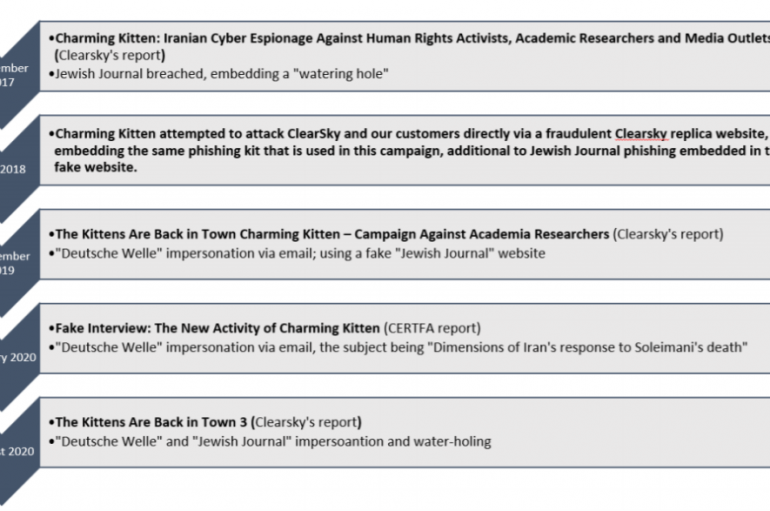
The Iran-linked Charming Kitten APT group leveraged on WhatsApp and LinkedIn to carry out phishing attacks, researchers warn. Clearsky security researchers revealed that Iran-linked Charming Kitten APT group is using WhatsApp and LinkedIn to conduct spear-phishing attacks. Iran-linked Charming Kitten group, (aka APT35, Phosphorus, Newscaster,
US Moves to Forfeit 280 Crypto Accounts
US Moves to Forfeit 280 Crypto Accounts The United States is trying to forfeit 280 cryptocurrency accounts tied to cyber-attacks on two virtual currency exchanges, which were allegedly perpetrated by North Korean threat actors. According to a civil forfeiture complaint filed by
DNC Warns Staffers of Romance Scam
DNC Warns Staffers of Romance Scam The Democratic National Committee sent out a nationwide alert on Wednesday warning romance-seeking campaign staffers to be wary of what information they reveal to people they match with on dating apps. Staffers were instructed to “swipe
Housemates Regularly Share Access to Online Accounts Nearly half (46%) of people are comfortable sharing streaming services with members of their households, according to a new study by Kaspersky. The analysis also showed that a third (33%) of those surveyed
Fake Login Page Detections Top 50,000 in 2020
Fake Login Page Detections Top 50,000 in 2020 Over 50,000 fake login pages were detected in the first half of 2020, with some able to be polymorphic and represent different brands. According to research from Ironscales, fake login pages are commonly
30+ #COVID19 Spam Emails Analyzed Every Minute
30+ #COVID19 Spam Emails Analyzed Every Minute A COVID-19 domain is blacklisted every 15 minutes, while 35 COVID-19 spam emails are analyzed per minute. That’s according to research by RiskIQ, which determined the top threats in 2020 and discovered that
Walmart Announces Surprise TikTok Bid
Walmart Announces Surprise TikTok Bid The saga over TikTok’s forced sale to a US company took another turn late this week after it emerged that Walmart is joining Microsoft’s bid for the firm. Branded a national security threat by the
Musk: Tesla Was Target of Russian Ransomware Conspiracy Elon Musk has confirmed that Tesla was the target of a ransomware conspiracy to infect a Nevada-based company revealed this week. The multi-billionaire technology entrepreneur tweeted yesterday in response to a news
Empire Market Falls After Suspected Exit Scam
Empire Market Falls After Suspected Exit Scam Rumors are rife that one of the dark web’s largest English language marketplaces has been hit by an exit scam, potentially shattering trust in underground sites like it. Empire Market, which sells everything
APT Hackers Using Malicious Autodesk 3ds Max Software Plugin to Hack Architecture Firm Systems
Recently, the APT hackers exploited a vulnerability in the conventional 3D computer graphics Autodesk software in sequence to begin a new cyber-espionage attack on the systems of the international architectural and video creation companies. Researchers have detected this vulnerability and