Archive
Sophos patched a SQL injection flaw with XG Firewall product that exploited by attackers in the wild. Sophos informed about the bug on April 22, 2020, further analysis revealed that hackers can attack systems with either the administration interface (HTTPS
Operating Systems can be detected using Ping Command, Ping is a computer network administration software utility, which used to find the Availability of a host on an Internet Protocol (IP) network. Ping operates by sending Internet Control Message Protocol (ICMP)
With this article, we list some of the common web application attacks, impacts, and possible mitigation. In part -3 we are covering the following attacks. Cross-site scripting Cacheable Pages Discovered Referrer Header Not Properly Validated Cross-Site Request Forgery HTTP Headers
Beware of Zoom Phishing Campaign that Threatens Employees Contracts will be Suspended or Terminated
A new zoom phishing campaign observed asking recipients to join a zoom meeting that threatens employees that their contracts will be either suspended or terminated. The recipients are presented with a fake Zoom login page that asks recipients to input
Hackers Selling $2 Million Worth South Korean & US Payment Card Details in The Underground Darknet Market
Researchers detected a dump containing details for nearly 400,000 payment card records uploaded to a popular darknet card shop on April 9. The database was comprised almost entirely of the payment records related to banks and financial organizations in South
Hackers Spreading Hoaxcalls DDoS Botnet by Exploiting an Unpatched ZyXel RCE 0-Day Bug Remotely
Researchers uncovered a new variant of Hoaxcalls Botnet that spreading through exploiting the unpatched remote code vulnerability that resides in ZyXEL Cloud CNM SecuManager. Zyxel Cloud CNM secuManagr is a network management software designed to provide an integrated console to
Qihoo 360’s Netlab Researchers observed Moobot botnet has successfully spread in fiber routers for remote code execution using0-day vulnerability. There is a total of 9 vendors are affected by the same vulnerability, it is likely most of the vendors are
A new Zoom flaw lets hackers record Zoom meeting sessions and to capture the chat text without the knowledge of meeting participants’ even though host disables recording option for the participants. Zoom is an online video communication platform that has
Coalfire Acquisition Signed Off
The acquisition of cybersecurity firm Coalfire by funds advised by Apax Partners was officially finalized. Coalfire, a provider of cybersecurity advisory and assessment services, today announced that its acquisition was now complete following full regulatory approval. The financial terms of
Around 38% of people never update their passwords, according to a survey by Specops Software which has revealed some concerning trends regarding password safety. Another finding was that a third of the population use the same password for streaming services
Two-thirds of remote workers in the UK haven’t received cybersecurity training over the past year, raising fears that they may be more susceptible to attacks as hackers adapt their tactics during the current crisis. Norwegian app security firm Promon polled
Google warns that nation-backed hackers are exploiting the COVID-19 pandemic to organizations involved in the fight against the pandemic. Google is warning that nation-state actors are exploiting the COVID-19 (Coronavirus) pandemic to target health care organizations and entities involved in
Twitter has been forced to take down thousands of breached email addresses and passwords from US and global health organizations first disseminated by alleged Neo-Nazi groups. Rita Katz, director of SITE Intelligence Group, said the log-in combos were linked to
The UK’s mobile and finance industries have teamed up with GCHQ’s National Cyber Security Centre (NCSC) to better detect and block SMS phishing attempts designed to capitalize on the COVID-19 crisis. Known as smishing, these attacks use similar social engineering
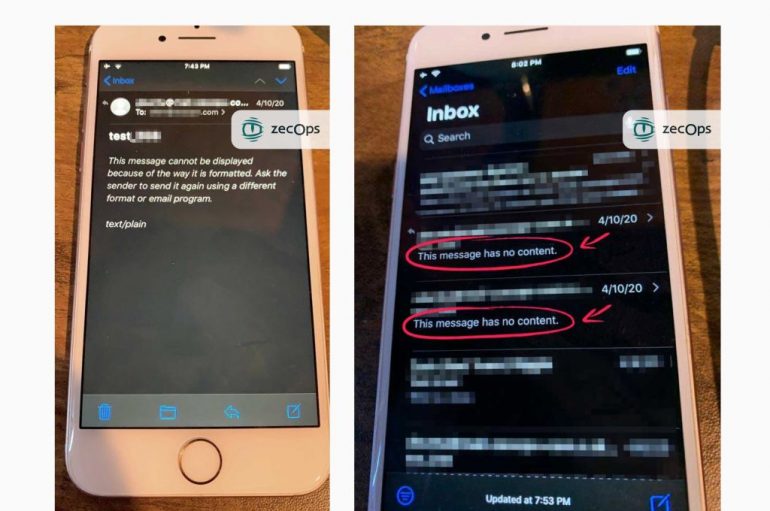
Two Zero-day Flaws With Apple iPhones and iPads Let Attackers to Hack Devices Just by Sending Emails
Security researchers from ZecOps discovered two zero-day vulnerabilities with default email mailing app present in Apple iPhones and iPads let attackers take over the devices by just sending an email. The vulnerability has been exploited by attackers since at least
Two zero-day flaws in the default mailing app pre-installed on iPhones and iPads allow attackers to hack the devices just by sending emails. Experts at cybersecurity firm ZecOps have discovered two zero-day vulnerabilities in iPhone and iPad devices that have been