Archive
New research into malware affecting mobile devices has found that stalkerware and adware posed the biggest threat to users in 2019. The annual “Mobile Malware Evolution” report, published yesterday by Kaspersky, shows a significant increase in the number of attacks
Nation states are actively attacking digital and internet-connected assets, but whether or not the US and other governments are doing enough to stop those attacks is a burning question that was debated in a session at the RSA Conference in
Registration opened for the National Cyber League (NCL) Spring Season this week. The NCL is a biannual cybersecurity competition for high school and college students aimed at training and mentoring the next generation of cybersecurity professionals. The NCL invites students
Met Police Boss Slams Facial Recognition Critics
The head of London’s Metropolitan Police has fiercely defended her force’s use of live facial recognition (LFR) technology, arguing that privacy rights have changed in an age of social media and that some critics are “highly ill-informed.” Speaking at think
Ransomware Detections Surged 10% in 2019
Trend Micro blocked over 52 billion unique cyber-threats in 2019, 61 million of which were ransomware, according to its annual roundup report. The security firm revealed that email remained by far the most popular threat vector, accounting for 91% of
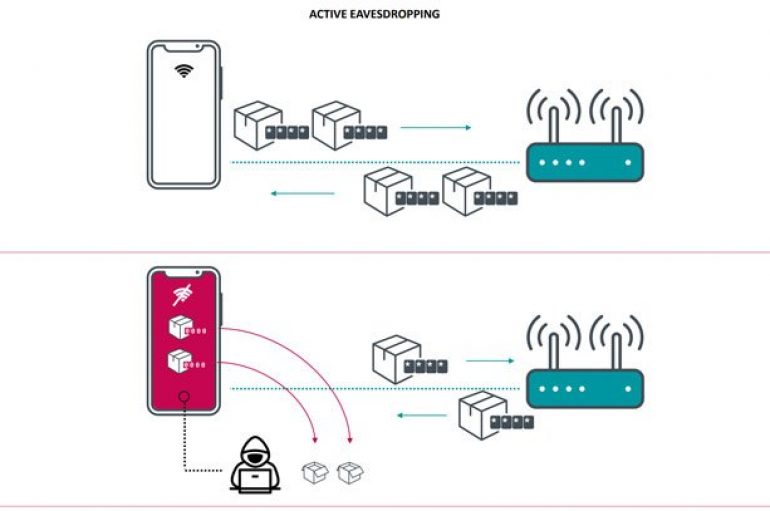
A high-severity hardware vulnerability, dubbed Kr00k, in Wi-Fi chips manufactured by Broadcom and Cypress expose over a billion devices to hack. Cybersecurity researchers from ESET have discovered a new high-severity hardware vulnerability, dubbed Kr00k, that affects Wi-Fi chips manufactured by
What is DNS Attack and How Does it Works?
DNS Attack is a type of cyber attack that exploits the weakness or vulnerability in Domain name system. Today, the internet has turned into an integral part of our life. From communicating to banking to shopping to traveling, every aspect
Google Released a Patch for Chrome Zero-day Vulnerability That Actively Exploited in Wide
Google Chrome issued an emergency patch to fix 3-high security vulnerabilities including a zero-day bug that actively exploited in wild. All the vulnerabilities are patched with Chrome version 80.0.3987.122 and the update is available for Windows, Mac, and Linux users.
In an era when data breaches can lead to corporate losses and ruin brand reputations, cybersecurity is no longer just an IT issue, it’s a board-level issue The question of what corporate boards should be doing and how governments can
At RSA Conference in San Francisco, Steve Lipner, executive director of SAFECode, reflected on some of the mistakes he has made in 50 years of working in IT and cybersecurity. In a talk he introduced as “things I wish I’d
Ordnance Survey Breach Hits Employee Data
UK mapping agency Ordnance Survey has suffered a security breach leading to the compromise of data on 1000 employees, according to reports. The government body is said to have discovered the incursion and immediately remediated the problem back in January.
Tech vendor Zyxel addresses a critical vulnerability in several network-attached storage (NAS) devices that is already being exploited in the wild. Zyxel has released security patches to address a critical remote code execution vulnerability, tracked as CVE-2020-9054, that affects several NAS
UK Financial Watchdog Admits Data Blunder
The UK’s Financial Conduct Authority (FCA) has admitted exposing the personal data of its critics online. The FCA, whose job it is to regulate the conduct of the approximately 59,000 financial services firms and financial markets in the United Kingdom,
Researchers discovered major vulnerabilities in several Free VPN apps for Android that allow attackers to perform dangerous Man-in-the-Middle Attacks and steal usernames, passwords, photos, videos, messages and more. There are several VPN’s caught in this list that downloaded more than
At BSides San Francisco, Bryan Zimmer, head of security at Humu, delivered a talk on how to create a security program and develop a security-centric culture as the organization’s first security hire. “So you’re the first security hire,” began Zimmer.
#BSidesSF: Keynote: Slack CISO Reflects on a Decade of Mayhem and Gives Checklist Advice in Its Wake
At BSides San Francisco, Larkin Ryder, the interim CISO at Slack, delivered a keynote based on a decade of retrospection, reflection, and prediction. Ryder broke down her observations on the past ten years of cybersecurity into the following notable categories: