Archive
Hackers share SQL databases from unsecured AWS buckets, including the archive belonging to the BGR tech news site in India. Hackers are sharing SQL databases from unsecured Amazon S3 buckets, one of them belongs to the BGR tech news site
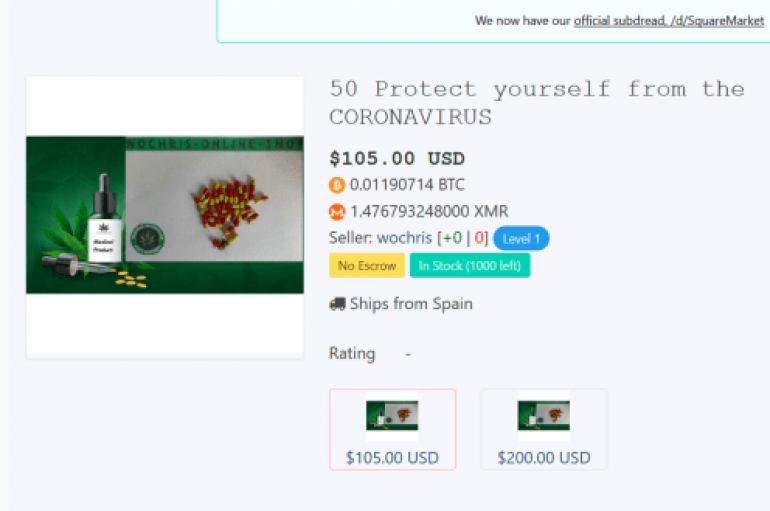
Hunting the Coronavirus in the Dark Web
Let me share with you the result of a one-night long analysis of major black marketplaces searching for anything related to the coronavirus epidemic. Recently I have received many questions from journalists and colleagues about the activity in the dark
Academic researchers discovered a new form of IMPersonation Attacks in 4G LTE networks called IMP4GT allowed attackers to exploit the missing integrity protection for user data and injecting malicious Arbitary packets by impersonating the victims. 4G Long Term Evolution (LTE)
Google revealed that the enhancements to its scanning system implemented in Gmail are boosting its detection capabilities. Google announced that the new scanning capabilities implemented in Gmail have increased the detection rate of malicious documents. The IT giant proudly announced
A controversial facial recognition company has just informed its customers of a data breach in which its entire client list was stolen. Clearview AI leapt to fame in January when a New York Times report claimed that the start-up had
A notorious group behind digital skimming attacks has upped its game recently, infecting at least 40 new websites, according to researchers. Magecart Group 12, one of many collectives using techniques designed to harvest card details from e-commerce websites, continues to
Now is the time to review your exposure to GDPR and CCPA-related lawsuits, and review contracts related to penetration testing. In a talk at RSA Conference in San Francisco exploring recent cyber-related court cases, Julia Bowen, senior vice-president, general counsel
A Guide to Building a Cyber Security Strategy On Your Organization Against The Security Breach
Everything that can be hacked will be hacked, or at least someone will try. Over the past few years, we have seen massive data breaches where hackers have stolen petabytes of confidential and often personal data from companies that customers
Kr00k – New Wi-Fi Vulnerability Let Hackers Decrypt WPA2-Encrypted Traffic – Billion of Devices Affected
Kr00k, a security flaw in Wi-Fi chips allows attackers to decrypt the WPA2-encrypted traffic. The vulnerability affects Broadcom and Cypress chips, these are the most common chips used by several client devices including top brands such as Amazon (Echo, Kindle),
It’s time to get rid of parental controls and let younger people make their own decisions. Speaking in the opening keynotes at the RSA Conference in San Francisco, Wendy Nather, head of advisory CISOs, Duo Security at Cisco, said that
Speaking at the RSA Conference in San Francisco on how to build a comprehensive Internet of Things (IoT) security testing methodology, Rapid7 IoT research lead Deral Heiland said that it is currently hard to determine what IoT is, so he
How can the US deter other nations from executing cyber-attacks? According to a panel of US government officials speaking at the RSA Conference in San Francisco, there is a range of legal, diplomatic, and even military options that can be
Cyberattacks can impact individuals and companies in different ways, but few if any industries have the same life-or-death impact as medical devices. In recent years, medical devices and hospitals have come under increasing attack from different threat actors, which has
Australian Federal Police (AFP) could be given powers to cyber-spy and hack into online computer systems used by criminals based in Australia under a new proposal being considered by the country’s federal government. Suggested changes would allow the AFP to
US DoD Adopts Ethical AI Principles
The US Department of Defense announced yesterday that it has adopted a series of ethical principles regarding the use of artificial intelligence (AI). Designed to build on the US military’s existing ethics framework, which is based on the US Constitution,
As more and more of our personal lives are stored digitally, our computers can effectively become extensions of ourselves. Everything from our fondest memories to our darkest secrets can be stored digitally. The issue arises then with making sure that