Archive
The United Arab Emirates denied reports that the popular mobile app ToTok was used as part of a government massive surveillance program. According to a report recently published by the New York Times, the popular app ToTok was used by
3 Critical RCE Vulnerability That Affects Ruckus Wireless Routers Let Hackers Exploit the Routers Remotely
A security researcher discovered a 3 critical remote code execution vulnerabilities in Ruckus Wireless routers let malicious hackers bypass the routers and take control of it remotely. Ruckus Networks are known as selling wired and wireless networking equipment and software.
Experts uncovered a new tool dubbed BIOLOAD used by the FIN7 cybercrime group used as a dropper for a new variant of the Carbanak backdoor. Security experts from Fortinet’s enSilo have discovered a new loader, dubbed BIOLOAD, associated with the
In September Zynga, the American social game developer running social video game services suffered a data breach that 173 Million accounts. Zynga Inc is an American social game developer running social video game services founded in April 2007, it primarily
FIN7 Hackers Added New Hacking Tool BIOLOAD to Evade AV Detection – Attacks Windows 64-bit OS
Researchers observed a new tool attributed to the FIN7 hacker group dubbed BIOLOAD aimed to minimize the footprint in the victim machine and to avoid detection. The new tool has similarities with FIN7’s BOOSTWRITE tool that abuses the DLL search
Thai Officials Confirmed the Hack of Prison Surveillance Cameras and the Video Broadcast
Authorities in Thailand are investigating a cyber attack that resulted in the broadcast of surveillance video from inside a prison in the country’s south. Local media reported that hackers broke into the surveillance system at Lang Suan prison in the
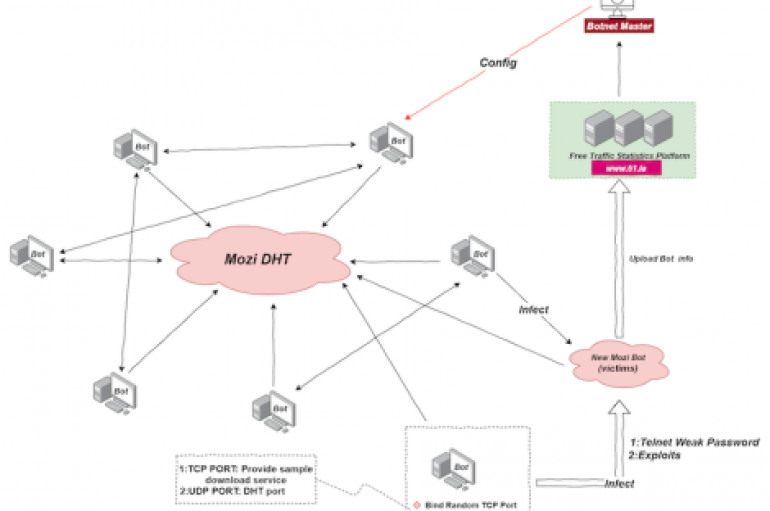
A new Distributed Hash Table (DHT) protocol based botnet dubbed Mozi attacks routers with weak passwords and known exploits. The botnet appears to be active at least from September 03, 2019. DHT is a decentralized distributed that provides lookup service
Critical SQLite vulnerabilities named “Magellan 2.0” discovered in World’s most popular browser Google Chrome let hackers exploit the Chromium render process and execute the remote code. SQLite is a well-known database that widely used in popular embedded database software, and
A flaw in the Twitter app for Android could have been exploited by attackers to obtain sensitive information or take over an account. Twitter has recently addressed a security vulnerability that affected the Android version of the app, it could
A new Mozi P2P botnet is actively targeting Netgear, D-Link, and Huawei routers by probing for weak Telnet passwords to compromise them. Security experts from 360 Netlab spotted a new Mozi P2P botnet that is actively targeting Netgear, D-Link, and
A popular mobile app in the Middle East called ToTok has been removed from both Apple and Google’s online stores because it was a spy tool. According to a report published by the New York Times, the popular app ToTok
Critical Vulnerability in Citrix Products Let Hackers Access to 80,000 Companies Internal Network
A researcher discovered a critical vulnerability in Citrix Application Delivery Controller (NetScaler ADC) & Citrix Gateway (NetScaler Gateway) let external hackers access to the company’s local network remotely. Experts believe that at least 80,000 companies could have affected around the
Russia’s government announced that it has successfully concluded a series of tests for its RuNet intranet aimed at country disconnection from the Internet. The Russian Government has announced on Monday that it has successfully concluded the test on its RuNet
Operation Wocao – New hidden Chinese threat groups are known as APT20 targeting various private, and government networks using custom hacking tools and various tactics and techniques. Threat groups likely support the Chinese government to gather sensitive data from other
Cyber-Attack Grounds Flights in Alaska
RavnAir Group was forced to ground flights on Saturday following a cyber-attack on the Alaskan company’s computer network. In a statement released on Saturday morning, RavnAir wrote: “On Friday, December 20th, RavnAir Group experienced a malicious cyber-attack on our company’s
Citrix Vulnerability Puts 80K Companies at Risk
A critical flaw has been discovered in two Citrix products, placing 80,000 companies in 158 countries at risk. The easily exploitable vulnerability could allow attackers to obtain direct access to a company’s local network and to access a company’s credentials.