Archive
Dangerous Function in UC Browser Lets Hackers to Hijack Millions Of Android Users via MITM Attacks
Potentially dangerous future in UC browser puts Hundreds of millions of Android users under high risk that allows hackers to hijack Android devices via Man-in-the-Middle Attacks. A hidden future that uncovered in UC browsers let attackers download and run untested
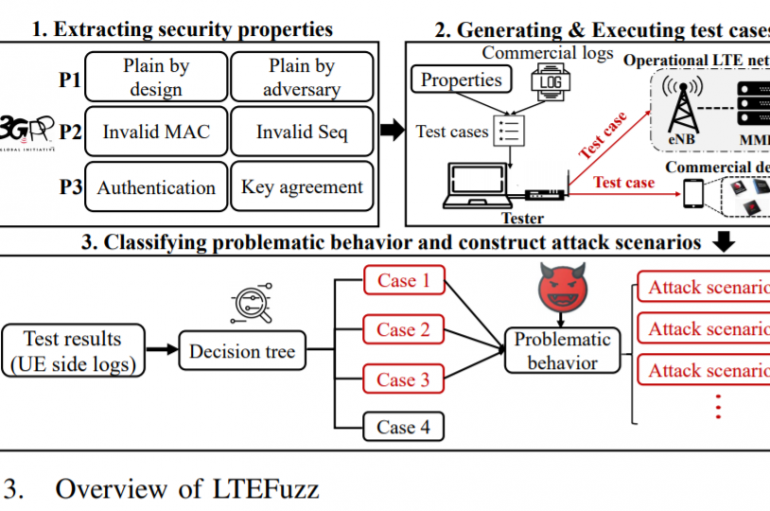
A team of researchers from the Korea Advanced Institute of Science and Technology Constitution (KAIST) discovered 36 vulnerabilities in the LTE protocol. Security experts from the Korea Advanced Institute of Science and Technology Constitution (KAIST) have discovered 36 vulnerabilities in
Experts from Kaspersky observed a new C++ version of the AZORult data stealer that implements the ability to establish RDP connections. The AZORult Trojan is one of the most popular data stealers in the Russian cybercrime underground. The AZORult stealer
According to MalwareBytes’s 2019 State of Malware Report, Trojans and crypto miners are the dominate malware threats of 2019. Android phones may get infected with malware less often than Windows computers, but that doesn’t mean they’re not vulnerable. With more
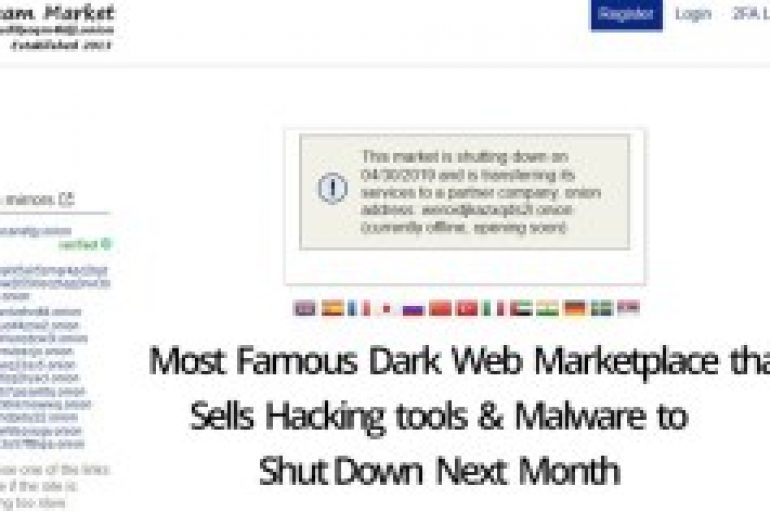
Most Famous Dark Web Marketplace that Sells Hacking tools & Malware about to Shut Down Next Month
Largest and notorious dark web marketplace Dream Market announced that it is scheduled to shut down its operation’s on April 30, 2019. Dream market has been for six years, it is was the largest market place in the dark web
Norsk Hydro is still in the process of restoring its IT systems after a devastating ransomware attack last week which has already caused the firm as much as GBP40m ($41m). The Norwegian firm, one of the world’s largest producers of
The NETSCOUT Threat Intelligence team uncovered a credential harvesting campaign tracked as LUCKY ELEPHANT targeting mostly South Asian governments. Security experts at NETSCOUT Threat Intelligence team uncovered a credential harvesting campaign, tracked as LUCKY ELEPHANT, targeting mostly South Asian governments. The
Computer Forensics tools are more often used by security industries to test the vulnerabilities in network and applications by collecting the evidence to find an indicator of compromise and take an appropriate mitigation Steps. Here you can find the Comprehensive
A new free cyber threat Intelligence tool that helps you in identifying malicious IP addresses and domains. It provides you a clean and easy to understand dashboard and it rates top attackers IP address, attacked ports, malicious domains, scanners, and
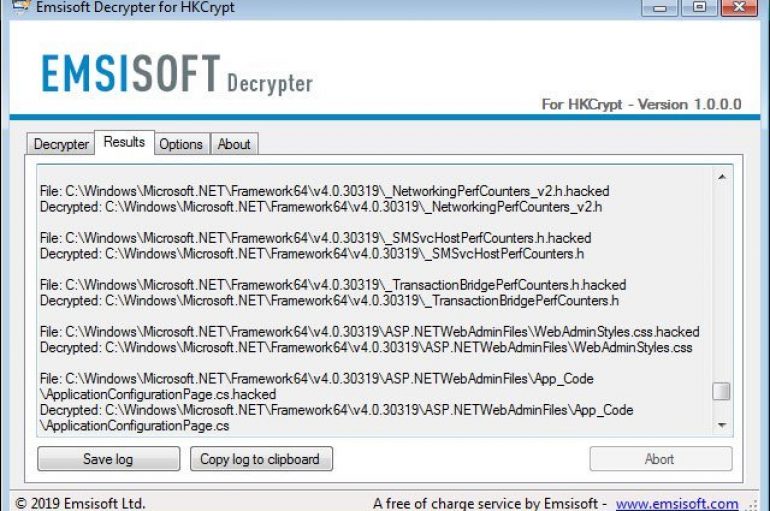
Good news for the victims of the Hacked Ransomware, the security firm Emsisoft has released a free decryptor to decrypt the data of infected computers. Security experts at Emsisoft released a free decryptor for the Hacked Ransomware. The Hacked Ransomware
The Recent Widely Spreading Lockergoga Ransomware Infection Can Be Stopped by Creating a Shortcut (LNKfile)
Lockergoga infection was first spotted in January 2019, the ransomware particularly targets on critical infrastructure. The Lockergoga ransomware encrypts all the files in the system and appends .locked extension and leaves a ransom note in the desktop folder. It was
So Long and Farewell: Dream Market Says Goodbye
Cyber-criminals have long relied on the Dark Web’s largest marketplace, Dream Market, to buy and sell illicit goods, but today threat researchers at IntSights and Flashpoint found that the notorious online store is scheduled to shutdown on April 30, 2019.
Over half (52%) of IT and security professionals believe that cybersecurity skills shortages are putting their business at an increased risk of attack, according to a new poll from Infosecurity Europe. Now in its 24th year, Europe’s leading cybersecurity show
Most Security Pros Are Impacted by Geopolitics
Two-thirds of cybersecurity professionals have been forced to change where and with whom they do business because of escalating concerns around nation state attacks, according to Tripwire. The security vendor polled 218 security professionals at the RSA Conference in San
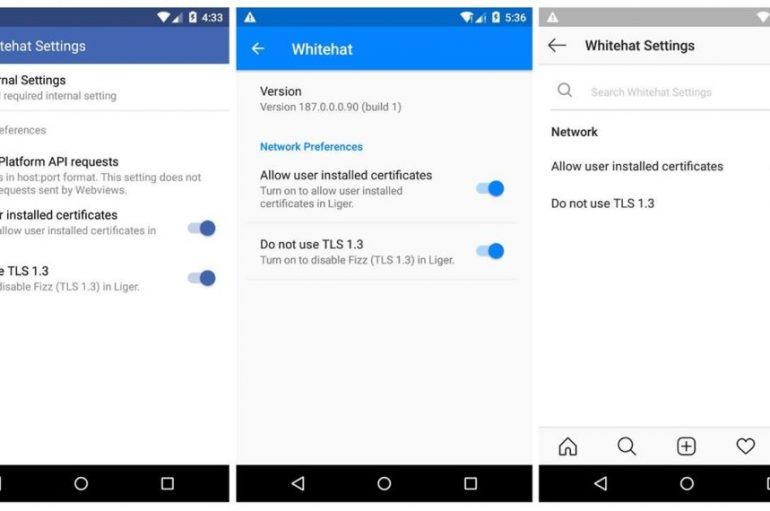
Facebook introduced new settings designed to make it easier for cyber experts to test the security of its mobile applications. Facebook has announced the implementation of new settings to make it easier for white hat hackers to test the security
Telegram Now Allows You to Delete All Your Private Messages Anytime from both Sender & Receiver
Telegram now landing into the peak of the privacy and let users delete their entire private messages from both sender and receiver side regardless of the time limit. Telegram is one of the most trusted platform and the one who