Archive
There has been a decline in ransomware infections, but that does not mean that earned revenue has reduced for cyber-criminals. According to the third instalment of the Check Point 2019 Security Report, threat actors are increasingly targeting public cloud and
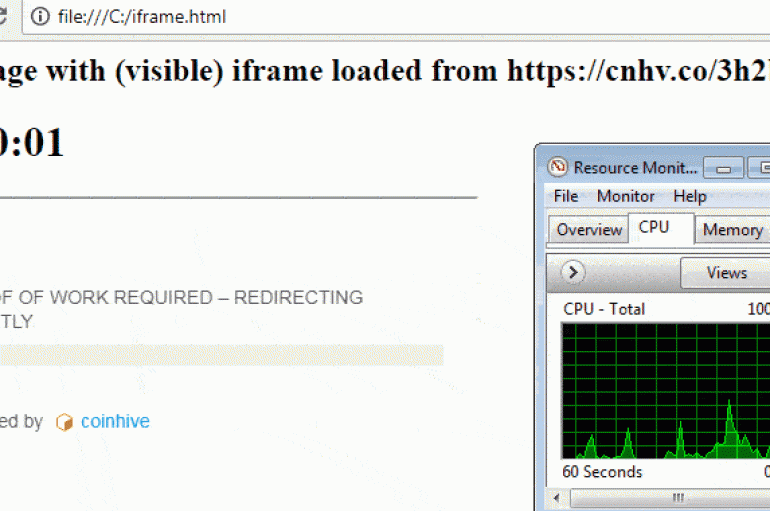
The popular in-browser cryptocurrency mining service Coinhive has announced that it will shut down on March 8, 2019. The service made the headlines across the years because it was used by crooks to abuse computational resources of the victims that were
Web Application Security Poses Greatest Risk
The majority of vulnerabilities in 2018 were associated with network vulnerabilities, while less than 20% were associated with web applications and APIs, according to the fourth annual Vulnerability Stats Report from Edgescan. When it comes to breaches, though, web application
Almost three million UK businesses could be exposing themselves to cyber-threats by having unknown devices on their network, according to new Forescout research. The security vendor polled over 500 IT decision makers in the UK to better understand their exposure
Most US Firms Expect Critical Attack this Year
An estimated 80% of US businesses expect to be hit by a critical security breach at some point in the coming year, according to new research from Trend Micro. The security giant polled over 1000 IT security professionals to compile
2018: The Year of Next-Generation Attacks
Enterprises around the globe are facing a new breed of cyber-attacks that are largely fueled by geopolitical tensions, according to Carbon Black‘s 2019 Global Threat Report. Last year cybersecurity professionals struggled to defend against increasing crypto-mining attacks, along with fileless
Only 28% of Advisories Help Mitigate Risks
In its second annual review of vulnerabilities and threat group activity specific to industrial control systems (ICS), Dragos found that the majority of the public vulnerability advisories it tracked in 2018 were network exploitable. The Year in Review is comprised
Free Tool: Honey Feed
Cybersecurity expert Marco Ramilli shared another tool of his arsenal that extracts suspicious IPs from undesired connections, his HoneyPots. Hi folks, today I’d like to point you out another tool of mine which extracts suspicious IPs from undesired connections. In
Takuya Yoshida from Toyota’s InfoTechnology Center and his colleague Tsuyoshi Toyama are members of a Toyota team that developed the new tool, called PASTA (Portable Automotive Security Testbed). PASTA is an open-source testing platform specifically designed for car hacking, it
Despite a 28% decrease in cybersecurity startups during 2017, global venture capital funding for cybersecurity rebounded with record high investments, according to Strategic Cyber Ventures. Though last year saw $5.3 billion in cybersecurity global ventures, Strategic Cyber Ventures called this
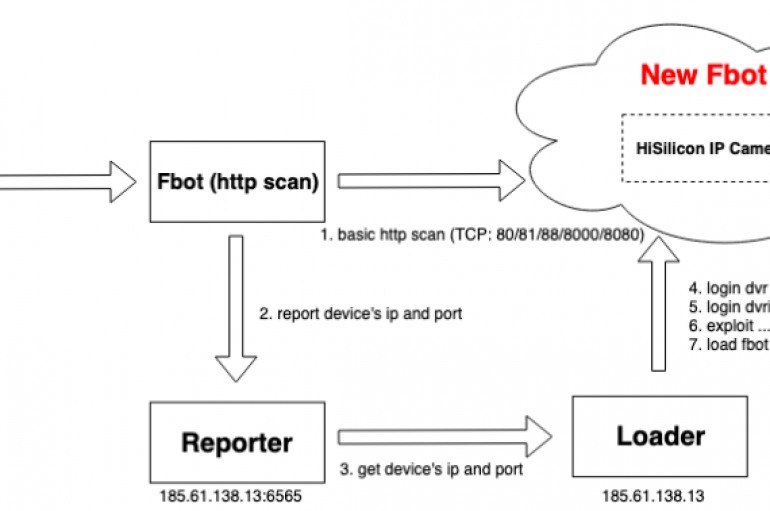
Experts at 360Netlab observed the Fbot bot infecting a large number of HiSilicon DVR/NVR Soc devices. Since February 16, 2019, security experts at 360Netlab observed a large number of HiSilicon DVR/NVR Soc devices were infected with an updated version of
Group-IB experts discovered new databases with a total of 69,189 Pakistani banks’ cards that have shown up for sale on the dark web. Group-IB, an international company that specializes in preventing cyberattacks, has discovered new databases with a total of
Researchers at Duo Labs has launched a new service called CRXcavator that allows users to analyze Chrome extensions and deliver security reports on them. Researchers at Duo Labs, a division of Duo Security, has launched a new service called CRXcavator
Experts discovered a critical vulnerability in the British Airways Entertainment System. The flaw is a privilege escalation issue that resides in the component USB Handler, an attacker could exploit it using an unknown input to escalate privileges. The affected British
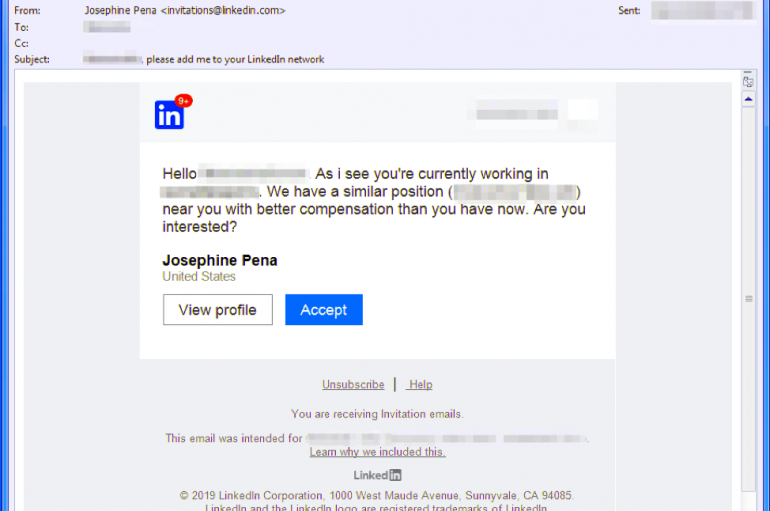
Experts uncovered a new malware campaign that attempts to circumvent victims by abusing LinkedIn ‘s direct messaging service. Researchers at Proofpoint have uncovered a new malware campaign that attempts to circumvent victims by abusing LinkedIn’s direct messaging service. “In direct
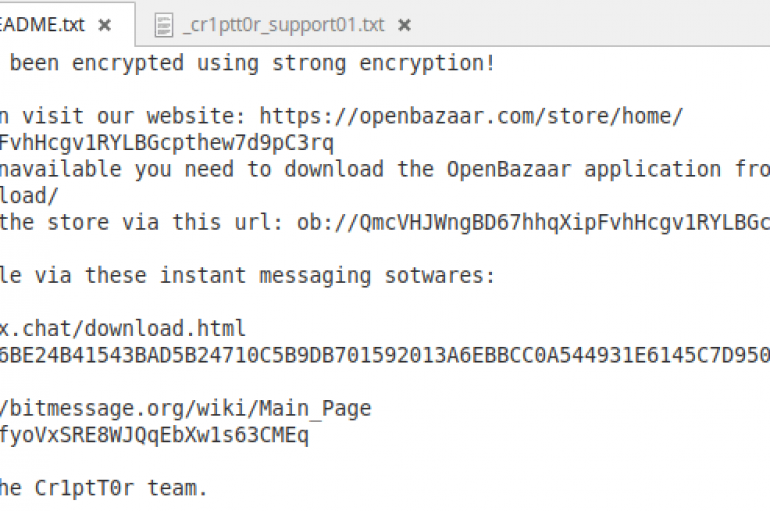
A new piece of ransomware called Cr1ptT0r infects embedded systems and network attached storage (NAS) devices exposed online. A new piece of ransomware called Cr1ptT0r was discovered by experts, it infects embedded systems and network attached storage (NAS) devices exposed