Archive
Privacy Legislation Might Have Stopped Facebook
In the aftermath of an extensive New York Times investigation into Facebook’s data privacy regulations and whether the company violated the privacy and public policy regulations of the Federal Trade Commission, Sen. Amy Klobuchar (Minn.) said that it is time
Caribou Coffee notified customers a payment card breach that hit more than 260 of its stores in the United States. A payment card breach hit over 260 Caribou Coffee stores, the company owned by German JAB Holding Company detected the
Criminal Charges Filed in DDoS-for-Hire Services
Efforts to take down multiple domains that offered distributed denial-of-services (DDoSs) for hire were successful and resulted in another announcement from the Justice Department (DOJ), which yesterday declared that it had seized 15 internet domains, as well as filed criminal
Air Force Fixes 120 Bugs, Pays $130K in Bounties
The US Air Force‘s third bug bounty program has concluded after a month-long hacking period, which ran from October 19 to November 22, 2018. As a result of their research findings, hackers were awarded more than $130,000 in bounties. According
Singapore Launches Second Bug Bounty Program
The agency at the helm of Singapore’s digital services, the Government Technology Agency of Singapore (GovTech Singapore), announced that Singapore will be working with security researchers over the course of three weeks on a bug bounty program intended to further
IBM Kernel-Based Vulnerability Discovered
Researchers have discovered a kernel-based vulnerability in a driver bundled with IBM Trusteer Rapport for MacOS, according to a recently published advisory from Trustwave. If exploited, the vulnerability could elevate privileges on the local machine, allowing an attacker to subvert
Researchers at Palo Alto Networks discovered that the Russian-linked Sofacy APT has written a new version of their Zebrocy backdoor using the Go programming language. The Sofacy APT group has been active since at least 2007 and it has targeted
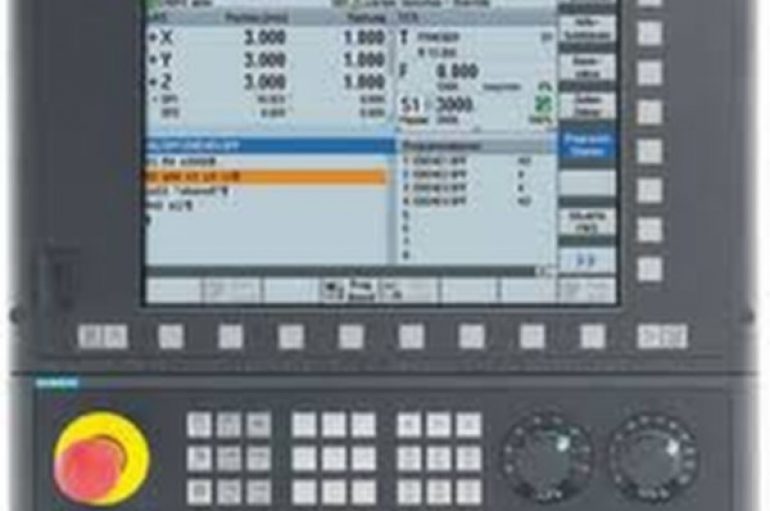
Siemens addressed several vulnerabilities in SINUMERIK controllers, including denial-of-service (DoS), privilege escalation and code execution issues. Siemens has fixed several flaws in SINUMERIK controllers, some of them have been classified as “critical.” The list of vulnerabilities includes DoS, privilege escalation
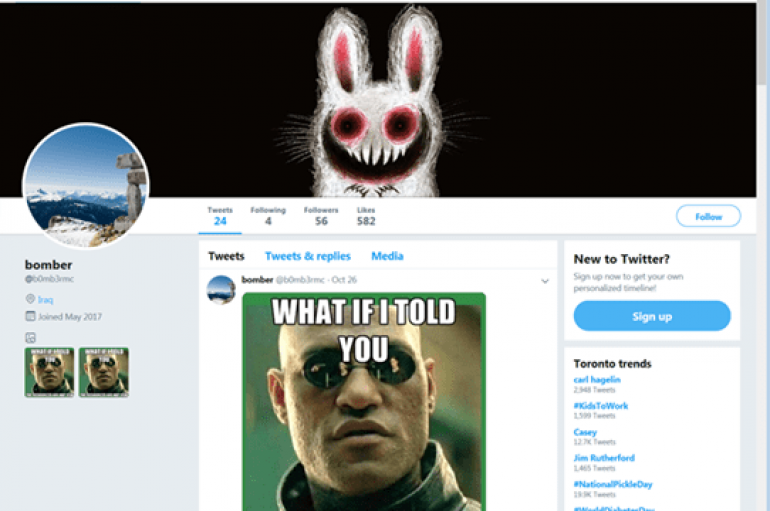
Security researchers at Trend Micro have spotted a new strain of malware that retrieved commands from memes posted on a Twitter account controlled by the attackers. In this way, attackers make it hard to detect traffic associated with the malware
Email Security Systems Miss 17K Threats
In its latest Email Security Risk Assessment (ESRA), Mimecast found that incumbent email security systems inaccurately deemed nearly 17,000 dangerous files “safe” this quarter. Email scams have been on the rise, which is partly what prompted Mimecast to dig into
PewDiePie Hackers Hijack Printers Again
Printers around the world appear to have been hijacked again with a message to subscribe to a popular YouTube vlogger, and improve their cybersecurity. Those behind the attack are thought to be the same ones that managed to get a
Save the Children Hit by $1m BEC Scam
A leading children’s charity was conned into sending $1m to a fraudster’s bank account this year, in another example of the dangers of Business Email Compromise (BEC). Save the Children Federation, the US outpost of the world-famous British non-profit, revealed
Researchers have discovered a new version of ThreadKit, malware known to be used by Cobalt Group, first identified in 2016, according to Fidelis Cybersecurity. In the recently released report, Fidelis threat research analysts found that despite reported arrests, Cobalt Group
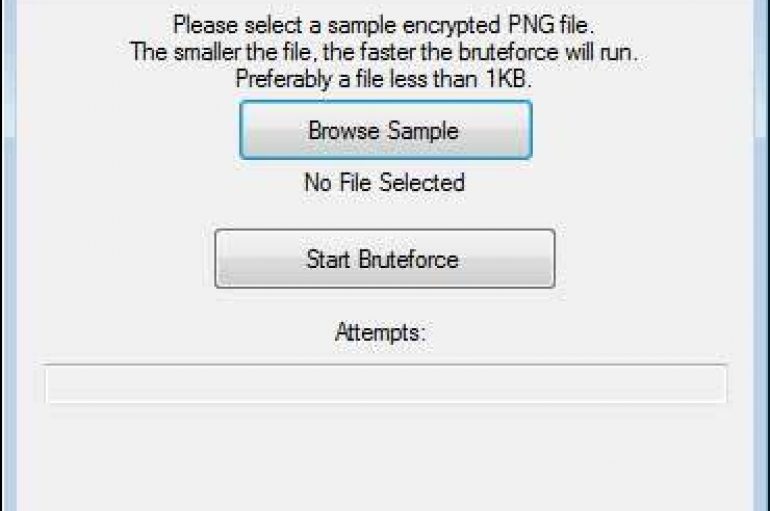
Good news for the victims of the dreaded HiddenTear Ransomware, the popular cybersecurity expert Michael Gillespie has devised a tool dubbed HT Brute Forcer that could allow decrypting files for free. In 2015, the Turkish security researchers Utku Sen published
Security experts at Palo Alto Networks uncovered a new espionage campaign carried out by Russia-Linked APT group Sofacy. Russian Cyber espionage group Sofacy (aka APT28, Pawn Storm, Fancy Bear, Sednit, Tsar Team, and Strontium)) carried out a new cyber campaign
US DoD Inspector General’s report revealed United States’ ballistic missile defense systems (BMDS) fail to implements cyber security requirements. The U.S. Department of Defense Inspector General published a report this week that revealed that lack of adequate cybersecurity for the