Archive
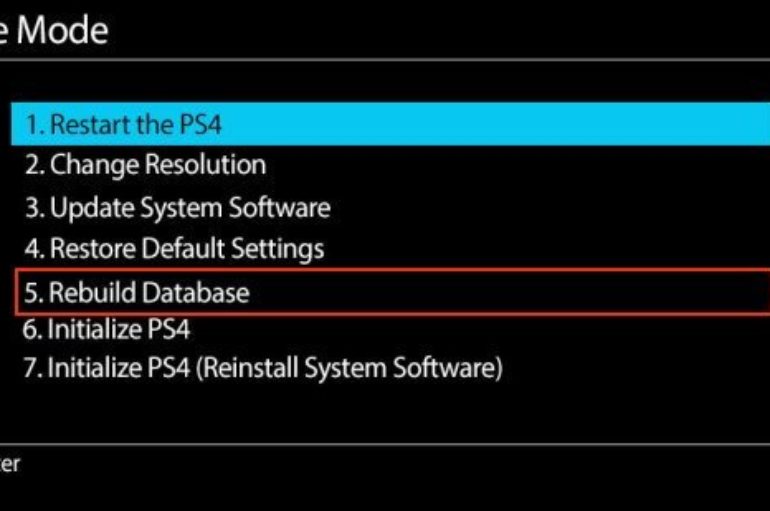
PlayStation 4 gaming consoles could crash when they receive messages containing certain symbols from fellow gamers. The consoles could freeze on while the owners are playing their preferred games, the DoS condition is triggered while the devices are parsing symbols
iPhone a Growing Target of Crypto-Mining Attacks
Apple has increasingly been the target of crypto-mining attacks, and according to Check Point, iPhone attacks increased by nearly 400% over the last two weeks in September. In its most recently published Global Threat Index, Check Point researchers said they
Attack Vectors Long Quiet Make Loud Q3 Comeback
Cyber-criminals eased into the year with a somewhat quiet first and second quarter, but according to a new report from Malwarebytes, attackers made some noise in Q3 2018. In the Cybercrime, Tactics and Techniques Q3 2018, researchers found that business
WannaCry Cost NHS GBP92 Million
The infamous WannaCry ransomware campaign of 2017 caused losses in the region of GBP92m for the NHS, the government has revealed. In a progress update titled Securing cyber resilience in health and care, the Department of Health and Social Care
Hackers Win Big by Gambling on Identity Spoofing
In analyzing global cybercrime patterns ThreatMetrix found that identity spoofing, fueled by stolen identity data, is the most prevalent attack vector for the gaming and gambling industry. Additionally, the Q2 2018 Gaming & Gambling Report discovered that location (IP) spoofing
Organizations globally are suffering a crippling cybersecurity workforce “gap” of 2.9 million employees today, putting the majority at greater risk of attack, according to the latest estimates from (ISC)2. The global certifications body has introduced a new gap analysis methodology,
One in 10 Reported Emails Verified as Malicious
New findings from Cofense have revealed that one in ten reported emails in 2018 were malicious, with more than 50% of those linked to fraudulent attempts to gather login and system information from users – known as credential phishing. As
Best Antivirus Software: 13 Top Tools
The AV-TEST Institute recently tested the most popular Windows 10 client antivirus products on three primary criteria: protection, performance, and usability. Only five of the 18 products tested earned a perfect rating of 6 for each of those criteria: Bitdefender
The number of compromised credentials detected in North American botnets has soared 141%, according to the latest quarterly analysis from Blueliv. The cyber-threat intelligence vendor scans the open, deep and dark web for signs of stolen log-ins for its clients,
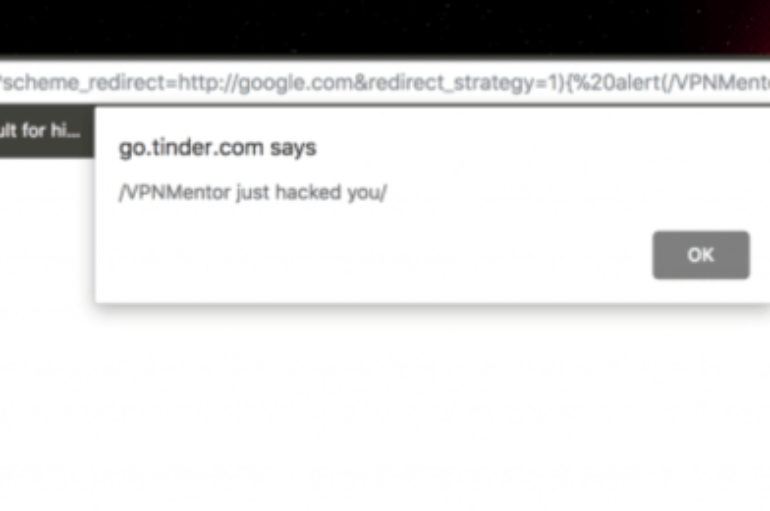
More than 685 million users may have been exposed to XSS attacks due to a flaw in Branch.io service used by Tinder, Shopify, and many others. Security Affairs was the first to publish the news of a DOM-XSS Bug Affecting
Security Staffing Low in Midsized and Large Orgs
Security Staffing Low in Midsized and Large Orgs One of the greatest security challenges for midsized to large organizations is a function of staffing, according to research conducted by Osterman Research on behalf of ProtectWise and published in The Evolving State
USB Threats from Malware to Miners
Introduction In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98% of the dropped drives were picked up by staff and students, and at least half
Security experts from Palo Alto Networks have collected evidence that links the recently discovered NOKKI malware to North Korea-Linked APT. Researchers from Palo Alto Networks have spotted a new variant of the KONNI malware, tracked as NOKKI. that was attributed to North
Malware Less Common in Q2, Still Top Attack Method Despite malware attacks becoming less common since Q1 2018, they are still the top attack method, according to new research from Positive Technologies. In its Q2 2018 Cybersecurity Threatscape, Positive Technologies
Financial Sector Breaches Have Tripled Since 2016 US financial services firms suffered three-times more data breaches in the first six months of 2018 than during the same period in 2016, according to new data from Bitglass. The security vendor aggregated
Some common malware will attempt to gather information about its environment, such as public IP address, Language, and Location. System queries and identifier websites such as whatismyipaddress.com are often used for these purposes but are easily identified by modern network monitors and