Archive
A study on the state of software security released today by CA Veracode evidenced improvements in DevOps security, suggesting that DevSecOps is facilitating better security and efficiency. While the report shows promise on the development side, it also analyzed flaw
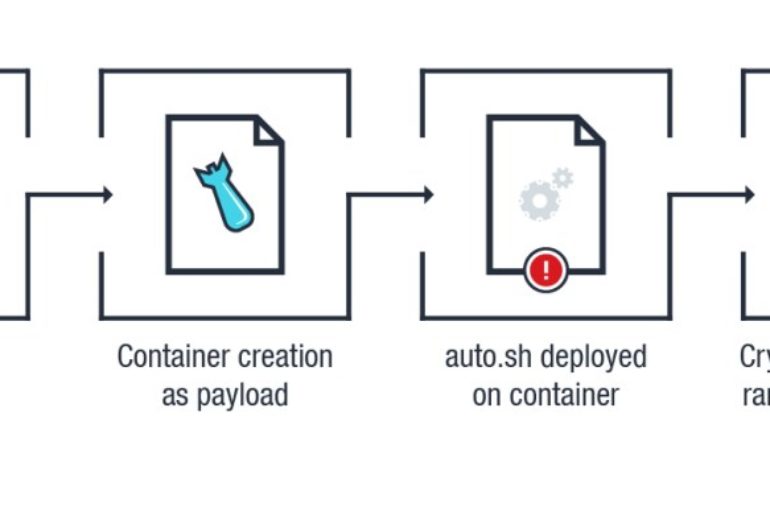
Cybercriminals continue to abuse unprotected Docker APIs to create new containers used for cryptojacking, Trend Micro warns. Crooks continue to abuse unprotected Docker APIs to create new containers used for cryptojacking. Earlier this year Sysdig and Aqua Security researchers started
Authors: Kaspersky Lab and the Oxford University Functional Neurosurgery Group There is an episode in the dystopian near-future series Black Mirror about an implanted chip that allows users to record and replay everything they see and hear. A recent YouGov
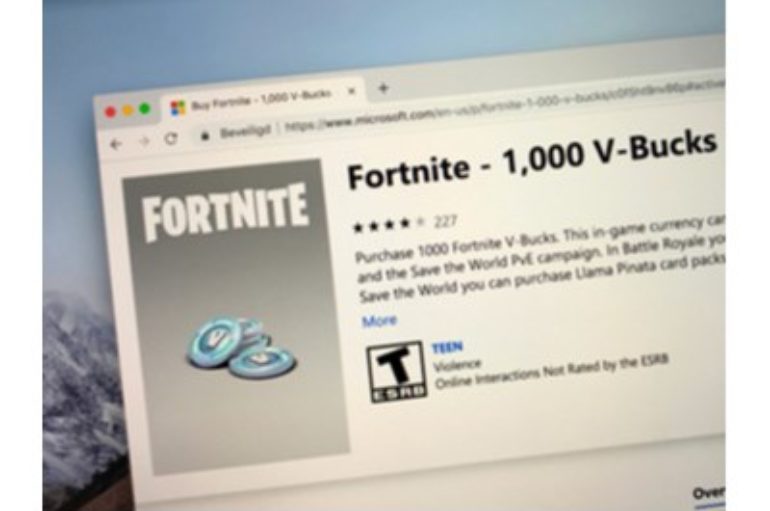
Hackers Target Fortnite with V-Buck Scams
According to new research released by ZeroFOX, Fortnite has become a hotbed for scammers targeting the in-game currency of the popular online game. Between early September and early October, ZeroFOX generated more than 53,000 alerts related to Fortnite scams, of
Customers of a little-known Canadian cryptocurrency exchange are set to lose all their coins after hackers allegedly made off with around $6m, although some suspect an exit scam. MapleChange took to Twitter on Sunday morning to claim that it had
IBM announced it is going to buy the open source company Red Hat for $34bn with the intent to enhance its cloud offerings. This is the biggest tech merger in history involving a software company. Red Hat was founded in
Researchers discovered a “high” severity command injection vulnerability, tracked as CVE-2018-15442, in Cisco Webex Meetings Desktop. It’s time to patch again the Cisco Webex video conferencing software of your organization to avoid ugly surprise. Researchers Ron Bowes and Jeff McJunkin
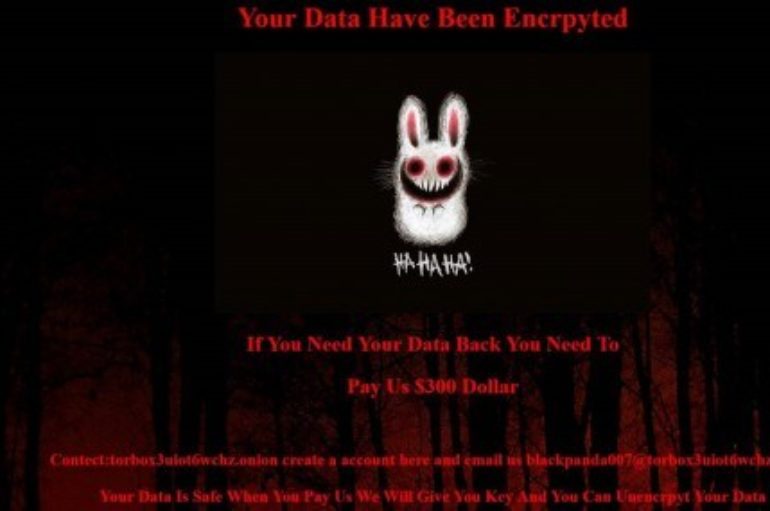
Good news for the victims of the infamous GandCrab ransomware, security experts have created a decryption tool that allows them to decrypts files without paying the ransom. Bitdefender security firm along with Europol, the FBI, Romanian Police, and other law
Experts Presented BOTCHAIN, The First Fully Functional Botnet Built Upon The Bitcoin Protocol
Security experts Antonio Pirozzi and Pierluigi Paganini presented BOTCHAIN, the first fully functional Botnet built upon the Bitcoin Protocol. Security expert Antonio Pirozzi, director at ZLab malware lab at Cybaze firm, presented at the EU Cyber Threat Conference in Dublin
Over a fifth (21%) of US consumers will never return to a brand that has suffered a data breach, according to new research providing a timely reminder of the need for effective cybersecurity. Contact center payments firm PCI Pal polled
The data breach suffered by the British Airways airline is worse than initially thought, according to IAG firm that wons the airline further 185,000 customers may have had impacted in the incident. The data breach suffered by the British Airways
ICS and IIoT Increasingly Vulnerable to Hackers
According to the 2019 Global ICS & IIoT Risk Report published by CyberX, cyber-criminals are increasingly targeting the vulnerabilities of industrial control systems (ICSs) and the industrial internet of things (IIoT). The report reflects the findings from data captured over
Demand for cryptocurrency skills has rocketed by over 1000% over the past two years, but a disconnect between cybersecurity and the fast-emerging sector is exposing organizations to greater risk, according to Trend Micro. The security vendor analyzed data from popular
CISOs Challenged by Budget and Rise in Attacks
Having a lack of influence in the boardroom is one reason why 84% of CISOs in North America believe there is no way to avoid a cybersecurity breach, according to a new report from Kaspersky Lab. Results from the report
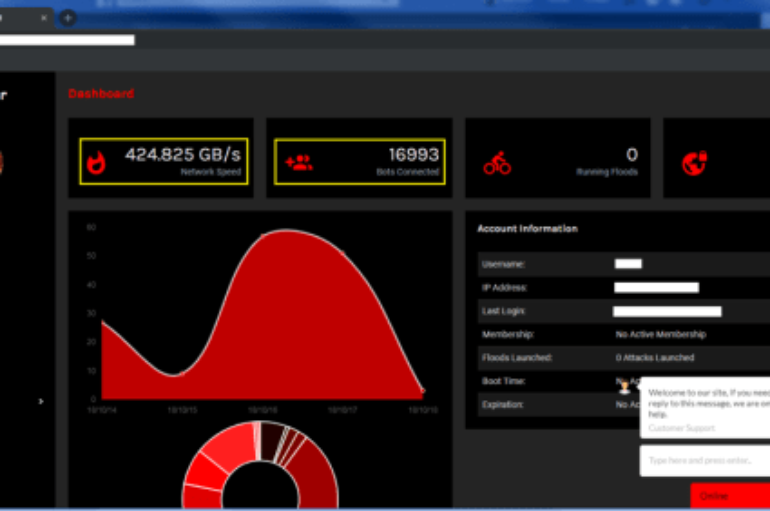
Security researchers at FortiGuard Labs have discovered a new DDoS-for-hire service called “0x-booter” built with leaked code that implements an easy to use interface. “0x-booter” first appeared on October 17, 2018, a post published on Facebook advertises over 500 Gbps
Introduction to Vulnerability Analysis and Vulnerability Scanning Tools: Vulnerability Assessment is also termed as Vulnerability Analysis. The method of recognizing, categorizing and characterizing the security holes (called as Vulnerabilities) among the network infrastructure, computers, hardware system and software etc is