Archive
We’re in an era in which pre-packaged exploit services make it possible for the average Joe, with no technological experience or prowess, to launch intricate attacks on our environments. So, what can be done? Patching operating systems and applications is
SWIFT said yesterday that there are no signs of foul play in its network or messaging systems following last week’s data dump by the Shadow Brokers. Shadow Brokers released several Windows exploits, which were allegedly stolen from the NSA and
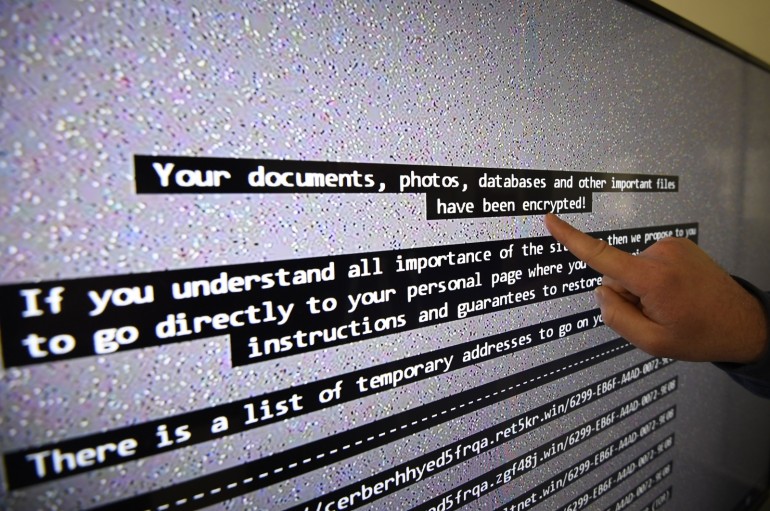
This new dark web ransomware-as-a-service is customised so any script kiddie can launch attacks
A new dark web ransomware-as-a-service (RaaS) has been uncovered by security researchers, which according to experts, is selling a new ransomware variant called “Karmen”. The customised ransomware is being sold by a Russian-speaking cybercriminal “DevBitox,” who goes by the username
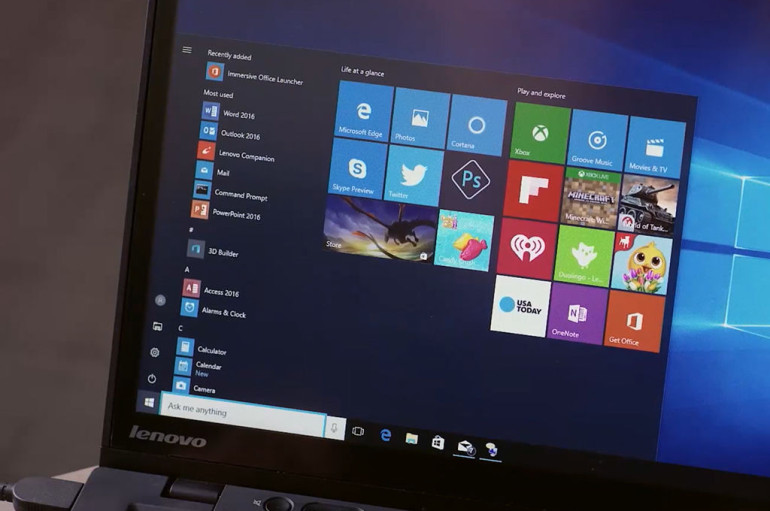
How to secure your Microsoft account
If you’ve installed Windows 10, or bought Microsoft Office, or set up an Outlook email address, chances are you’ve got a Microsoft account. This hub ties together everything you do with Microsoft’s software, from Cortana to OneDrive. With so much
The hacker group calling itself “Shadow Brokers” has made public another batch of files allegedly obtained from the NSA-linked threat actor tracked as the Equation Group. Microsoft has assured customers that these new exploits don’t affect up-to-date systems. The Shadow
Files released by the mysterious hacker Shadow Brokers suggested Friday the US National Security Agency had penetrated the SWIFT banking network and monitored a number of Middle East banks. The files, according to computer security analysts, also showed the NSA
5 Hot Enterprise Backup and Recovery Vendors
The data backup market is changing fast. Here are five vendors leading the transformation. The backup and recovery market has become a crowded space, with hundreds of vendors vying for market share. At the higher end of the market, the
As Ron Kehoe wrapped up his Data Center World session about Network Security Policy Management (NSPM) this past Wednesday, an attendee, sounding as though he had just learned about the Holy Grail of security, asked: “And, this technology is available
Training Courses
Technical Training Courses Looking for a course that fits your particular needs? Browse a catalog of the courses offered through the Fortinet NSE Institute where you’ll be able to select and learn more about any of the courses they offer.
Google Patches 31 Critical Flaws in Android
Google this week released security updates for Android to resolve numerous Critical remote code execution (RCE) and elevation of privilege (EoP) vulnerabilities in the platform. Over 100 vulnerabilities were resolved in Android this month, split into two separate sets of
Samsung’s Tizen OS Riddled With Security Holes
There are more than three dozen previously unknown flaws that pose a potential threat to consumers using some Samsung TVs, watches and phones, a security researcher reported Monday. Hackers could exploit the vulnerabilities found in Samsung’s Tizen operating system to