Petya Ransomware Outbreak
Less than two months after the disastrous, global WannaCry infestation, a variant of the Petya ransomware dubbed PetrWrap has started hitting companies in Russia, Ukraine, Spain, France, UK, India, and Europe and demanding $300 in bitcoins.
According to multiple sources, a new variant of Petya ransomware, also known as Petwrap, is spreading rapidly with the help of same Windows SMBv1 vulnerability that the WannaCry ransomware abused to infect 300,000 systems and servers worldwide in just 72 hours last month.
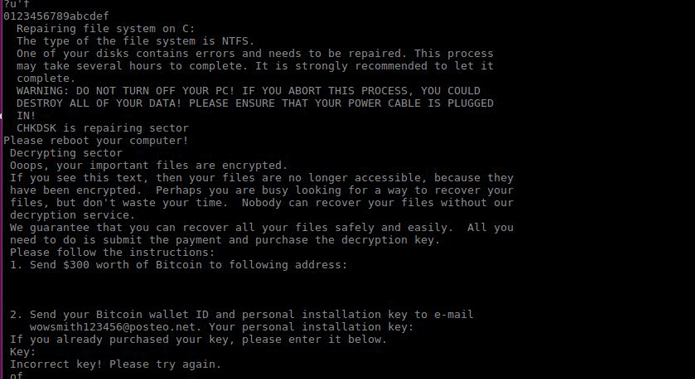
Petya is a nasty piece of ransomware and works by rebooting victims computers and encrypting the hard drive’s master file table (MFT) and rendering the master boot record (MBR) inoperable, restricting access to the full system by seizing information about file names, sizes, and location on the physical disk.
Petya ransomware replaces the computer’s MBR with its own malicious code that displays the ransom note and leaves computers unable to boot.
Apart from this, many victims have also informed that Petya ransomware has also infected their patch systems.
Screenshots of the latest Petya infection:
Petya ransomware has already infected the Russian state-owned oil giant Rosneft, Ukrainian state electricity suppliers, “Kyivenergo” and “Ukrenergo,” in past few hours.
There are reports from several banks, including National Bank of Ukraine (NBU) and Oschadbank, as well as other companies confirming they have been hit by the Petya ransomware attacks.
Maersk, an international logistics company, has also confirmed on Twitter that the latest Petya ransomware attacks have shut down its IT systems at multiple locations and business units.
EternalBlue is a Windows SMB exploit leaked by the infamous hacking group Shadow Brokers in its April data dump, who claimed to have stolen it from the US intelligence agency NSA, along with other Windows exploits.
Microsoft has since patched the vulnerability for all versions of Windows operating systems, but many users remain vulnerable, and a string of malware variants are exploiting the flaw to deliver ransomware and mine cryptocurrency.
Just three days ago, we reported about the latest WannaCry attack that hit Honda Motor Company and around 55 speed and traffic light cameras in Japan and Australia, respectively.
TO PROTECT YOURSELF:
Apply those patches against EternalBlue (MS17-010) Microsoft released (they will make you less susceptible if not completely protected) and disable the unsecured, 30-year-old SMBv1 file-sharing protocol on your Windows systems and servers.
Since Petya Ransomware is also taking advantage of WMIC and PSEXEC tools to infect fully-patched Windows computers, you are also advised to disable WMIC (Windows Management Instrumentation Command-line).
Researcher finds Petya ransomware encrypt systems after rebooting the computer. So if your system is infected with Petya ransomware and it tries to restart, just do not power it back on.
PT Security, a UK-based cyber security company, has discovered a Kill-Switch for Petya ransomware. According to a tweet, company has advised users to create a file i.e. “C:\Windows\perfc” to prevent ransomware infection.
To safeguard against any ransomware infection, always be suspicious of unwanted files and documents sent over an email and should never click on links unless they are from a verified source.
Have a good back-up routine in place that makes their copies to an external storage device that isn’t always connected to your PC.
Moreover, make sure that you run a good and effective anti-virus security suite on your system, and keep it up-to-date.
Here is the full list of countries affected by the attack as of the morning of 28 June, 2017:
Europe:
UK
Ukraine
Russia
France
Spain
Denmark
Germany
Poland
Belarus
Lithuania
Norway
Netherlands
Holland
Romania
Asia:
India
China
South Korea
North America
US
South America:
Brazil
Chile
Argentina
Middle East:
Turkey
Israel
Oceania:
Australia
New Zealand
Source | hackernews