Now Microsoft Office 2016 can block macro malware attacks
With macro-based malware infections on the rise, Microsoft has launched a new Office 2016 feature that can help enterprise admins neuter the threat.
Macros are disabled by default in Word, Excel and PowerPoint but attackers behind the banking malware Dridex and the more recent Locky ransomware have well-honed techniques to trick targets into enabling them, allowing malicious macros in email attachments to install malware on a PC.
Microsoft says despite periodic lulls in macro-based malware infections over the past year, they’re still increasing and that 98 percent of threats that target Office use malicious macros.
The main risk from macros stems from human curiosity sparked by email with attractive subject headers.
Microsoft noted in a report last year that, “It appears that users have become so accustomed to clicking the Enable content or similar warning bars in Microsoft Office products that they are now confident in being able to determine the perceived risk versus the potential gain.”
The new “tactical” security feature in Office 2016 allows admins to set scenario-based rules that block macros and prevent users from enabling them in high-risk situations, such as when documents arrive from the internet.
From Group Policy in Office 2016, admins can block macros for documents downloaded from cloud services such as Microsoft One, Google Drive and Dropbox.
If the organization uses Outlook and Exchange for email, macros in attached documents from outside the business can also be blocked. Finally, macros can be blocked for documents from public shares, such as file-sharing sites.
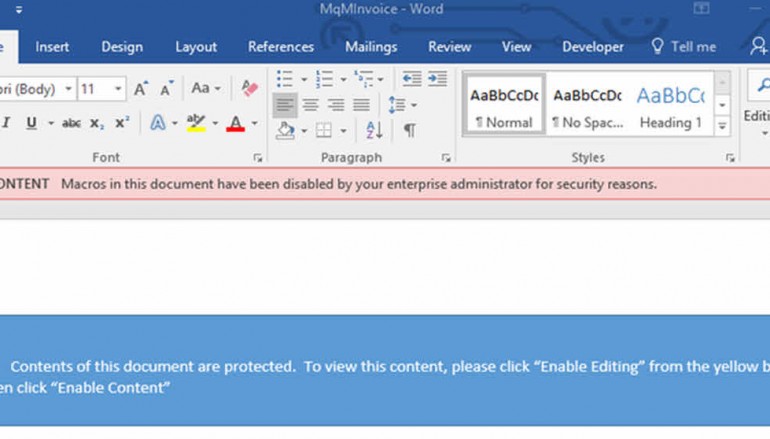
If an admin enables macro-blocking for all Office users, it will prevent users from exiting the Protected View sandbox when opening Word documents in Outlook. In Protected View, macros are disabled by default.
If an employee attempts to follow an attacker’s instructions and exit the sandbox mode, they will see a red-bar notification at the top of the document, stating that the administrator has blocked macros in this document. They also will not be able to exit Protected View.
Microsoft notes that if the policy impacts scenarios where macros are legitimately used, staff would need to work with admins to find alternative workflows.
Another enterprise security threat that Microsoft is addressing through Office is so-called CEO-spoofing, or business email compromise, which Snapchat and several other companies have fallen victim to in recent months.

Source | ZDNET





