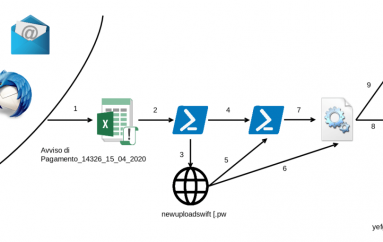
New malware takes advantage of Windows ‘God Mode’ to evade detection
The Windows “God Mode” tweak lets you quickly access a number of advanced functions — it’s a handy easter egg that has been a part of Windows for the last decade. However, McAfee researchers have now spotted a piece of malware that’s using the same folder renaming hack to hide from the user.
God Mode doesn’t technically create additional capabilities in the system, like its namesake did in the Doom games. Instead, it creates a creates a collection of useful control panel options in a “folder.” It’s not a regular folder, even though it starts as one. After creating a folder, you give it a name like GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}. That turns it into a “God Mode” link. It will no longer have a folder icon, and in fact, the system treats these directories differently than a regular folder.
McAfee says there’s a new variant of an existing piece of malware called Dynamer. When it’s installed on a system, it deploys itself in the AppData directory and places itself in a master control panel directory similar to God Mode. While God Mode is a commonly known system tweak, it’s not exactly an officially documented feature. Many tools and applications can’t access items that are concealed inside these pseudo-folders, a perfect place for malware to hide.
Even if the user is able to track down the file location of the mysterious executable, the modified folder just links back to RemoteApp and Desktop Connections control panel item with nothing of interest. The malware author took the deception a step further by using the folder name “com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}” Anything with the “com4” name is given special privileges in Windows; Explorer and cmd.exe treat the folder as a device, so it’s immune from standard console and file management commands.
So, it certainly sounds like all hope is lost, but there’s nothing magical or “godlike” about this malware. It’s just taking advantage of some Windows‘ oddities to confuse and misdirect. Dynamer can be removed in a few steps by killing the process from Task Manager. Then using a command prompt, enter “rd “\\.\%appdata%\com4.{241D7C96-F8BF-4F85-B01F-E2B043341A4B}” /S /Q.” That will delete the directory without confirmation, eliminating the malware.
This is hardly the only time a piece of malware has used Windows’ own peculiarities against it. If this becomes common, it will be interesting to see if Microsoft makes changes to prevent these sort of super-directories from being created so easily.
Source | Extremetech