
Canadian hospital’s website hacked to serve up Teslacrypt ransomware
A Canadian hospital’s website has been hacked in order to serve up the notorious Teslacrypt ransomware to unsuspecting visitors.
Jérôme Segura, a senior security researcher at Malwarebytes, explains in a blog postthat out-of-date server-side software is likely to blame for the site hack of Norfolk General Hospital, which is based in Ontario:
“The web portal is powered by the Joomla CMS, running version 2.5.6 (latest version is 3.4.8) according to a manifest file present on their server. Several vulnerabilities exist for this outdated installation, which could explain why the site has been hacked.”
To investigate the hack further, Segura had Malwarebytes’ honeypots visit the hospital’s website. The packet capture reveals that malicious code injected directly into the site’s source code redirected users to the Angler exploit kit, which in turn downloaded Teslacrypt ransomware.
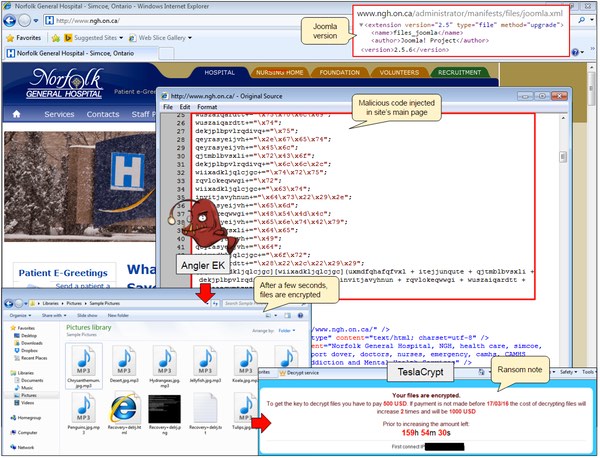
The case of Norfolk General Hospital is unusua; insofar as attackers are abusing its website to actually spread crypto-ransomware.
Elsewhere in North America, however, medical centers have triaged and treated similar types of malware found on their networks.
Perhaps the most well known case so far is when Hollywood Presbyterian Medical Center, a hospital located in southern California, temporarily declared an “internal emergency” and shut down its computer systems following a ransomware attack back in February.
Shortly following the infection, a local computer consultant said that the ransom fee was 9,000 BTC. At US $3.6 million, this would have been the largest malware-related ransom demand ever recorded. But the claim was incorrect.
Spokespeople for the hospital clarified that the real ransom fee was 40 BTC, or US $17,000. Ultimately, the hospital decided to pay the fee.
About a month later, news broke about a hospital located in Henderson, Kentucky that also declared an “internal state of emergency.”
Like Hollywood Presbyterian, the hospital determined that “Locky” ransomware was behind the infection. But unlike its California counterpart, the hospital allegedlyrestored its files via the use of a backup system and therefore did not pay the attackers a penny.
The Ottawa Hospital is also reported to have experienced a ransomware infectionrecently, only this time at the hands of a WinPLock variant. The medical center alsorecovered from the infection by restoring from unaffected backup.
All of these cases required system backups or ransom payments. By contrast, Norfolk General Hospital’s case is much simpler. All it needs to do is upgrade the version of Joomla it is using to run its web portal.
But even that simple step is proving to be too much trouble apparently.
 CBC reports that Segura checked the infected website a few days after reporting the hack to the hospital’s IT teams. Not only is their Joomla version still old and vulnerable, but apparently it has been rolled back to an earlier version that is older and even more vulnerable than the first.
CBC reports that Segura checked the infected website a few days after reporting the hack to the hospital’s IT teams. Not only is their Joomla version still old and vulnerable, but apparently it has been rolled back to an earlier version that is older and even more vulnerable than the first.
“If they don’t update it quickly, it will happen again,” Segura told CBC, adding that leaving the website in an outdated state is “just very irresponsible.”
To all sysadmins out there, you should always make sure that whatever software you use to power your web portals is up-to-date. This is especially true if you work at a hospital, where friends and family members of those who might not be in the best of health could experience additional suffering as a result of your inattention when they visit the hospital’s website.
Don’t be a jerk; update your systems.
Source | GrahamCluley





