Block malware, ransomware, and phishing with 5 layers
I spent last week in London at the InfoSec conference, where it wasn’t only the vendors talking up security scares, but the attendees I spoke with in the aisles and meeting rooms. Almost all of them had some personal experience with spear-phishing or a ransomware attack.
At InfoSec plenty of solutions were proffered to blunt such attacks, from point products to suites. It became clear that there are five key layers needed to defend your company from such attacks.
1. Email security gateway
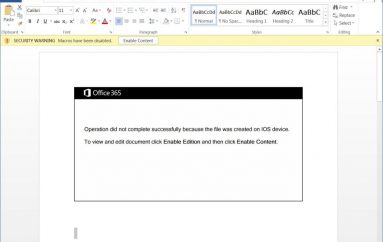
It’s obvious that the majority of breaches these days begin with an email. The email may contain a link to some kind of identity-theft site, instructions for a wire transfer, or a weaponized attachment. Spear phishing, whaling, ransomware, spam, and malware are all serious threats and nuisances that your organization faces.
You should have some sort of email gateway, be it a software based on-premises or a cloud-based tool or, alternately, an appliance. It’s best if you use a layered approach where you enhance what you already have, such as within Exchange or Exchange Online.
2. DNS security
The use of a DNS protection tool like OpenDNS is an oft-ignored option for fighting against attacks. Because every link a user clicks must reach out to a DNS server for resolution before the user can actually open the link, having a tool that can learn from all those clicks can provide a shield.
3. Endpoint protection
From a technical perspective, endpoint (client) protection is your last point of protection against attacks. Endpoint protection tools range from antimalware software to multifactor-authentications VPNs, and you’ll need more than one.
4. User behavior analytics
User behavior analytics tools watch for trends in your user base so that you can see when red flags come up, like a user who typically downloads 10 documents a day starting to download 1,000. There is no denying that Big Brother watching your organization is a key approach going forward in a world where more and more of the people attacking you are already on the inside and trusted to a degree.
5. Phishing testing and training
Raising awareness and increasing the education level of the user (your weakest link in security) is essential. Not surprising, there are tools to help. With such a tool, you can test your users on a regular basis to see how they react to real-world attacks, then require they take additional training (repeatedly). It’s the only way you can get them to be so paranoid about harmful links that they think twice before clicking.
In the end, a targeted attack may still get through all these layers. But by implementing all five layers, you minimize the chances of being a victim of such an attack.
Source | InfoWorld