Posts From Seid Yassin
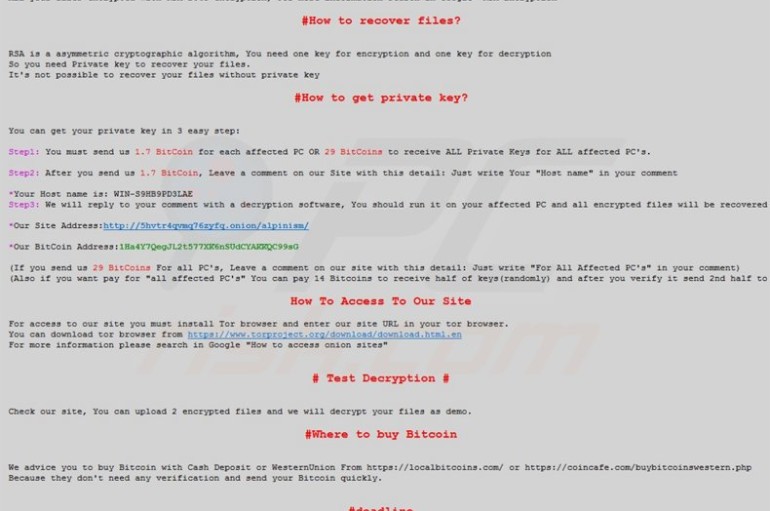
SamSam creators to date have raked in $6 million and the ransomware continues to be a thorn in the sides of organizations in both the public and private sectors. Peter MacKenzie, global malware escalations manager working in Sophos Technical Support,
Artificial Intelligence (AI) has been seen as a potential solution for automatically detecting and combating malware, and stop cyber attacks before they affect any organization. However, the same technology can also be weaponized by threat actors to power a new
The recently uncovered “Black” botnet campaign using the Ramnit malware racked up 100,000 infections in the two months through July– but the offensive could just be a precursor to a much larger attack coming down the pike, according to researchers,
Legacy Wi-Fi just became a little less safe: According to Jens Steube, the developer of the password-cracking tool known as Hashcat, has found a faster, easier way to crack WPA/WPA2-protected Wi-Fi networks. Hackers have compromised the WPA/WPA2 encryption protocols in
Linux Vulnerability Could Lead to DDoS Attacks
A Linux kernel vulnerability affecting version 4.9 and up could allow an attacker to carry out denial-of-service attacks on a system with an available open port, according to an Aug 6 security advisory from the CERT Coordination Center at Carnegie
Taiwan Semiconductor Manufacturing Company (TSMC)—Apple’s sole supplier of SoC components for iPhones and iPads, and Qualcomm’s major manufacturing partner—shut down several of its chip-fabrication factories Friday night after being hit by a computer virus. The world’s largest makers of semiconductors
Salesforce said in a post last week that it had alerted customers to a data leak caused by an API error. According to Salesforce, during an update to its Marketing Cloud service that was rolled out between June 4 and
HP Offers Up to $10,000 Rewards for Printer Bugs
HP launched a bug bounty program for printers Tuesday, with a max payout of $10,000 a vulnerability. The company, which has partnered with Bugcrowd to offer between $500 and $10,000 for bug discoveries, said that it marks the first-ever bug
A massive hacking campaign has been uncovered, compromising tens of thousands of MikroTik routers to embed Coinhive cryptomining scripts in websites using a known vulnerability. As of Thursday morning, Censys.io has reported more than 170,000 active MikroTik devices infected with
Drupal Patches Vulnerability in Symfony Library
Drupal issued an update to patch a vulnerability in its Symfony library that if exploited would give an attacker to gain access to higher level caches and web servers. The issue, CVE-2018-14773, effects many Symfony versions, 2.7.0 to 2.7.48, 2.8.0
Ransomware has become a multimillion-dollar black market business for cybercriminals, and SamSam being a great example. New research revealed that the SamSam ransomware had extorted nearly $6 million from its victims since December 2015, when the cyber gang behind the
Google recently removed 145 applications from Google Play after they were found to carry malicious Windows executables inside, Palo Alto Networks reveals. Most of the infected applications, Palo Alto’s researchers say, were uploaded to the application store between October and
A team of security researchers has discovered a new Spectre attack that can be launched over the network, unlike all other Spectre variants that require some form of local code execution on the target system. Dubbed “NetSpectre,” the new remote
Following Apple’s lead in banning cryptocurrency mining apps, Google has also updated its Play Store policy this week to ban apps that mine cryptocurrencies on users’ devices in the background. However, there are countless cryptocurrency mining apps, including MinerGate, AA
Researchers found 20 flaws in Samsung’s SmartThings Hub controller – opening up supported third-party smart home devices to attack. Researchers found 20 vulnerabilities in Samsung’s SmartThings Hub, allowing attackers to control smart locks, remotely monitor the home via connected cameras
The Hidden Bee cryptominer is being delivered to users via an improved drive-by download toolkit which exploits the CVE-2018-4878 Flash Player vulnerability. The Flash bug is a critical vulnerability that can potentially allow an attacker to take control of the