Archive
Yes, Google’s Project Zero team has once again publicly disclosed a vulnerability (with POC exploit) affecting Microsoft’s Windows operating systems ranging from Windows Vista Service Pack 2 to the latest Windows 10 that had yet to be patched. A few
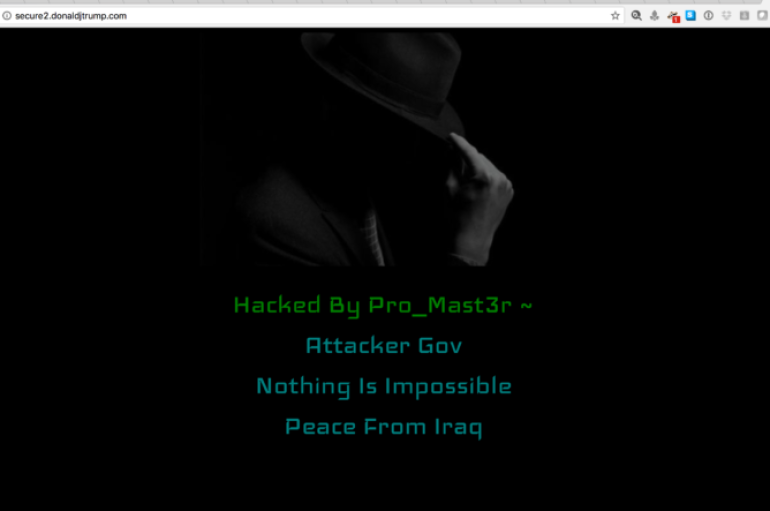
Someone calling themselves “Pro_Mast3r” managed to deface a server associated with President Donald Trump’s presidential campaign fundraising on Sunday, The server, secure2.donaldjtrump.com, is behind Cloudflare’s content management and security platform, and does not appear to be directly linked from the
Hackers can steal millions of cars after discovering huge flaw in manufacturer’s connected car apps
Security researchers have discovered that it is easy for attackers to gain access to millions of cars, simply by hacking into car-controlling mobile apps and using them to unlock the vehicles. Kaspersky Lab researchers Mikhail Kuzin and Victor Chebyshev decided
Self-Healing Malware Hits Magento Stores
Self-healing malware isn’t new, with the first such threat reportedly spotted nearly three decades ago, as the memory-residing Trojan called Yankee Doodle, which could infect .com and .exe files. Discovered in September 1989, this piece of malware would play the
FOR THE LAST decade or so, hackers have faced a daunting challenge when they try to break into a computer: Even when they get malicious code running on a victim’s machine, they have to figure out where in the computer’s
MEITU IS A popular app that transforms your selfie into an adorable anime character. You’ve probably already downloaded it. In exchange for the simple pleasure of giving you an absurd makeover, though, it demands sprawling access to your personal data
Kelihos Becomes King of the Malware Mountain
The beginning of 2017 has brought a series of changes on the malware charts, as the Kelihos botnet managed to climb to the top position, while the Conficker worm dropped to fourth on the list. An eight-year old threat, Conficker
WordPress blogs defaced in hack attacks
A security flaw in the WordPress blogging software has let hackers attack and deface tens of thousands of sites. One estimate suggests more than 1.5 million pages on blogs have been defaced. The security firm that found the vulnerability said
Self-destructing gadgets favoured by the likes of James Bond and Mission: Impossible’s Ethan Hunt have taken one step closer to reality. Researchers in Saudi Arabia have developed a mechanism that, when triggered, can destroy a smartphone or other electronic device
Norway Accuses Russia of Cyberattack
Oslo – Norway’s foreign ministry, army and other institutions were targeted in a recent cyberattack by a group suspected of ties to Russian authorities, Norwegian intelligence — which was among the targets — said Friday. Known as APT 29, the
There’s a zero-day exploit in the wild that exploits a key file-sharing protocol in most supported versions of Windows, including Windows 10, the latest and most secure version of the Microsoft operating system. The exploit is probably not worth worrying
Freedom Hosting II, the largest host of dark web sites has reportedly been hacked and taken down by a group of hackers allegedly associated with Anonymous. The hackers breached Freedom Hosting II’s servers and stole thousands of GB worth data,
World Cyber Security Congress 2017
Intel Security has fixed a critical vulnerability in its McAfee ePolicy Orchestrator (ePO) centralized security management product. Researchers warn that the flaw is ideal for profiling the users and infrastructure of an organization. The flaw, tracked as CVE-2016-8027 and assigned
A China-linked cyber espionage group has been using new malware and new techniques in attacks aimed at military and aerospace organizations in Russia and Belarus. In July 2016, security firm Proofpoint reported that the threat actor had been using NetTraveler
A recently observed phishing campaign is targeting PayPal users with fake pages that are well designed and difficult to distinguish from the real ones, ESET researchers warn. The attack was observed only a couple of weeks after Gmail users were