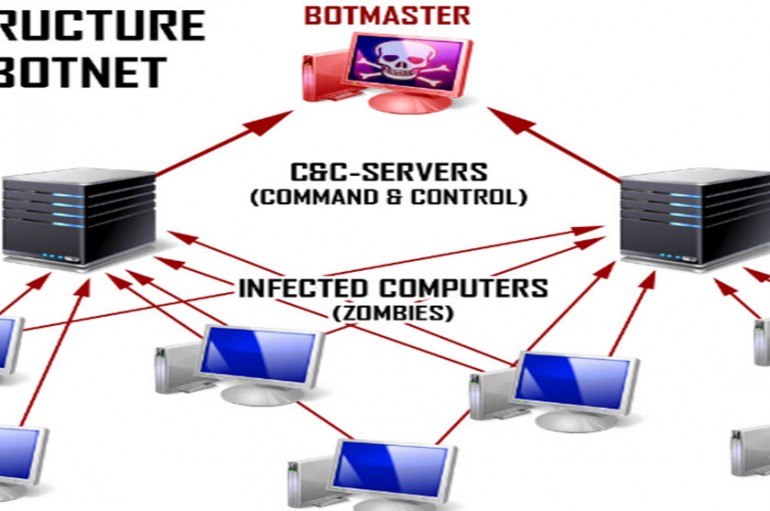
Archive
Before we get to best practices in botnet detection, let’s do a quick review of exactly what a botnet is. One of the most powerful ways to pursue any computationally challenging task is to leverage the untapped processing power of
The 5 Essentials of DDoS Mitigation
DISTRIBUTED DENIAL OF Service (DDoS) attacks are a real threat businesses and organizations deal with daily, but this does not mean they have to endure the slashes of service or slow downs attacks bring on. Organizations do not have to
“AMPing” up its security capabilities, Cisco integrates technology from its 2013 acquisition of SourceFire into its portfolio. Cisco revealed Feb. 24 that it is adding critical new security capabilities to its portfolio, thanks to technology gained via the $2.7 billion
ICS Security: Essential Firewall Concepts
While there are many benefits that have come to ICS and SCADA networks through the increased use of standard networking and Internet technologies, it has made the need to secure them ever more critical. Firewalls play an important role in
The Cloud Security Alliance is a multi-stakeholder effort that is all about (surprise, surprise) securing the cloud. While the CSA has been active for years, it’s still a challenge to keep up with cloud, as both use cases and cloud
Hackers who employ APTs (advanced persistent threats) are a different breed. A real and constant threat to the world’s companies and networks, APT hackers tend to be well organized, working together as part of a professional team. Their goal, typically,
Energy and electric utility organizations are facing a range of challenges requiring a reevaluation of the cyber security within their industrial control networks, endpoints and controllers. On the one hand, operators have to face losing access to phone lines, securing
The Internet of Things is gradually but very surely creeping in to impact every sphere of modern life. And that goes as much for people as for business, as much for new industries as for incumbent sectors. This network of
A criminal enterprise well known for using malware-laced fake display ads is ramping up its efforts by infecting dozens of popular websites using a recently patched Flash Player exploit to deliver the Angler Exploit Kit in a drive-by style attack.
The $3 billion IT security problem
Criminals are increasingly moving away from malware in favour of compromising business email to scam organisations out of money, security researchers are warning. Last month the FBI said social engineering had reaped attackers A$3 billion since October 2013, with over
Malware coders have adapted two Android trojans to cope with Marshmallow’s new user permission model, showing that despite Google’s best efforts, crooks will plow through all the company’s security measures and still reach their targets, even if in lesser numbers.
Malwarebytes tackles Mac malware, Reddit sidelines Imgur, Periscope saves your streams by default, SoundCloud Go gets cheaper for pro users, and how video games help siblings bond. Mac Malware Means Business Contrary to popular belief, Macs are not immune to
For most of the past year, Microsoft has largely refused to change controversial Windows 10 policies, no matter how unhappy a vocal minority of users were over the company’s new strategy. Telemetry tracking, mandatory updates that combine security and non-security
Dubai: There may be a silver lining to the recent increase in cyber attacks in the Middle East, according to Wael Mohammad, the president and COO of digital security firm TrendMicro. The obvious, although also worrisome, way to look at
Charging your mobile phone by plugging it into a computer could be enough to get you HACKED
When your phone starts complaining that its battery is running low, you probably wouldn’t think twice about plugging it into a computer to charge it up. But security experts claim that this simple act could be enough to get you
Security experts are fond of describing companies in one of two ways; those that have been hacked and those who don’t yet know they have been hacked. In LinkedIn’s case, unfortunately, it was both. As big data, the IoT, and